seemslikeadream » Thu Jul 27, 2017 8:41 am wrote:Google May Have Just Uncovered An Israeli Surveillance Start-Up Spying On Androids
Thomas Fox-Brewster, FORBES STAFF
Jul 26, 2017 8:40 PM 2,398
Google thinks Android users are being targeted with malware [+]
Google has found another malware targeting Android that it believes may be the product of the bustling Israeli surveillance scene. Whereas it previously found Android devices infected with malware it claimed came from NSO Group, it’s now detailed a spy tool it says is linked to a start-up called Equus Technologies.
Google found the malware, which it dubbed Lipizzan, sitting on fewer than 100 phones after one of them was already infected with the Pegasus malware associated with the NSO Group. “Lipizzan was a sophisticated two stage spyware tool,” its Android security team wrote in a blog post today.
Of the 20 different forms in which the spyware was delivered, Google found a handful on its Play store. Typically, Lipizzan would appear as a legitimate tool, such as a backup or sound recorder app. It rooted, monitored and stole user email, SMS messages, location and voice calls. The tool also sought to gather data from specific apps, undermining their encryption, including WhatsApp, Viber and Telegram, while LinkedIn, Gmail and Skype were also on its target list.
Google has now thrown the app developers off Play, while the offending apps have been removed from infected devices.
Forbes attempted to contact Equus employees over LinkedIn and email, but had not received a response at the time of publication. It does not have a website or any publicly available contact details.
Google said there were references to the firm in the code itself. Megan Ruthven, from Google’s Android security team told Forbes during the Black Hat conference in Las Vegas that a config file within the app mentioned the Equus name. She said that was an indicator, but not guaranteed attribution.
Lookout Mobile Security researcher Andrew Blaich, who presented on the malware alongside Ruthven, said there was likely attribution to Equus. NSO Group also left references to its Pegasus spyware in its code, he noted, while saying that they hadn’t yet gone down the “rabbit hole” of Equus. Despite the indicators, neither Ruthven or Blaich could say with certainty Equus was the true owner of the malware.
Who are Equus?
And mystery surrounds Equus.
Currently, it’s unclear if Google’s suggestion that Equus is a cyber arms company is accurate. From the limited information available online, Equus appears to be based just down the road from NSO Group in the Herzliya district of Tel Aviv. According to LinkedIn, at least one engineer moved from NSO to Equus this year. And the description of the company on LinkedIn reads: “Equus Technologies is a privately held company specializing in the development of tailor made innovative active cyber solutions for law enforcement, intelligence agencies, and national security organizations.”
The co-founders are listed on the networking site as former Israel Defense Forces researcher Matan Markovics and Tel Aviv University graduate Daniel Hanga. Markovics also used to ply his trade at another notable Israeli arms company, Rafael.
The company has given talks at ISS World Training, previously referred to as the Wiretappers’ Ball, where all manor of surveillance companies flog their gear. In 2015, it spoke on ‘Addressing the Growing Challenges of Cyber Intelligence’ during an ISS event in Prague, Czech Republic.
According to previous reports, earlier this year the company’s head of research, Amihai Neiderman, found an astonishing 40 zero-day vulnerabilities in Samsung’s Tizen operating system. They could have been exploited on Samsung smart TVs as well as cellphones. Neiderman also registered the site tizenhacker.com. It’s yet to have hosted any content, however.
Regardless of who Equus are and what link they have to the Lipizzan software, John Scott-Railton, a surveillance software researcher with Citizen Lab at the University of Toronto, said Google was doing fine work in providing a window into the “secretive but growing industry developing private malware.”
“A commercial spyware firm was trying to run below Google’s radar and deliver spyware across their platform. With this post, Google has said very publicly, ‘no you don’t.’” Pointing to recent reports of a proposed $400 million acquisition of 40% of NSO by Blackstone, Scott-Railton added: “This case highlights the risks that companies making commercial spyware may pose as investment opportunities as they run up against major companies’ commitments to protect their users.”
He’s been tracking NSO Group’s spread across Mexico, where it was recently seen targeting independent investigators looking into the mass disappearance of students in 2014. NSO didn’t deny it had sold to Mexico, but did express concern about any illegal use of its Pegasus software.
https://www.forbes.com/sites/thomasbrew ... lware/amp/
chump » Wed Oct 03, 2018 1:43 pm wrote:
https://citizenlab.ca/2018/10/the-kingd ... dian-soil/
THE KINGDOM CAME TO CANADA
How Saudi-Linked Digital Espionage Reached Canadian Soil
By Bill Marczak, John Scott-Railton, Adam Senft, Bahr Abdul Razzak, and Ron Deibert October 1, 2018
In this report, we describe how Canadian permanent resident and Saudi dissident Omar Abdulaziz was targeted with a fake package delivery notification. We assess with high confidence that Abdulaziz’s phone was infected with NSO’s Pegasus spyware. We attribute this infection to a Pegasus operator linked to Saudi Arabia.
Key Findings
• We have high confidence that the cellphone of Omar Abdulaziz, a Saudi activist and Canadian permanent resident, was targeted and infected with NSO Group’s Pegasus spyware. Abdulaziz has been outspoken on an ongoing diplomatic feud over human rights issues between Canada and Saudi Arabia. The targeting occurred while Abdulaziz, who received asylum in Canada, was attending university in Quebec.
• During our recently published global mapping of NSO’s Pegasus infrastructure, we identified a suspected infection located in Quebec, Canada, operated by what we infer is a Saudi Arabia-linked Pegasus operator. We matched the infection’s pattern of life to the movements of Abdulaziz, and his phone, with his assistance. After examining his text messages, we identified a text message that masqueraded as a package tracking link. This message contained a link to a known Pegasus exploit domain.
• We are unaware of any legal authorization for the infection and monitoring of Omar Abdulaziz in Canada by a foreign government. If not properly authorized, the operators behind this targeting may have committed multiple Criminal Code offences, including willfully intercepting private communications contrary to section 184(1).
1. Summary
Israel-based “Cyber Warfare” vendor NSO Group produces and sells Pegasus mobile phone spyware suite. Pegasus customers can infect targets using Androids and iPhones by sending them specially crafted exploit links. Once a phone is infected, the customer has full access to a victim’s personal files, such as chats, emails, and photos. They can even surreptitiously use the phone’s microphones and cameras to view and eavesdrop on their targets.
Over the past two years, multiple reports have emerged showing how Pegasus was abused by multiple NSO Group customers to target civil society. In 2016, Citizen Lab published the first report on the use of Pegasus, Million Dollar Dissident, which detailed how award-winning human rights defender Ahmed Mansoor was targeted, likely by the government of the United Arab Emirates. In 2017, Citizen Lab reported abusive uses of Pegasus spyware in Mexico, where targets included lawyers, journalists, and politicians. In August 2018, Amnesty International reported that a Saudi dissident based abroad (later revealed to be Yahya Assiri), as well as an Amnesty researcher, were targeted with Pegasus. In addition, former president Ricardo Martinelli stands accused by the government of Panama of having used Pegasus during his tenure between 2009 and 2014 to systematically spy on political opponents and journalists.
In a September 2018 report titled Hide and Seek, we detailed our investigation into the global proliferation of Pegasus operators and infections. After scanning the Internet for Pegasus servers and grouping the 1,091 servers we found into 36 distinct operators, we used DNS cache probing to query Internet Service Providers (ISPs) around the world and identified 120 ISPs in 45 countries where we suspected Pegasus infections were located (Figure 1). Our technique was based on the assumption that Pegasus infections regularly “phone home” to their command and control (C&C) servers to exfiltrate information and receive new commands from their operator.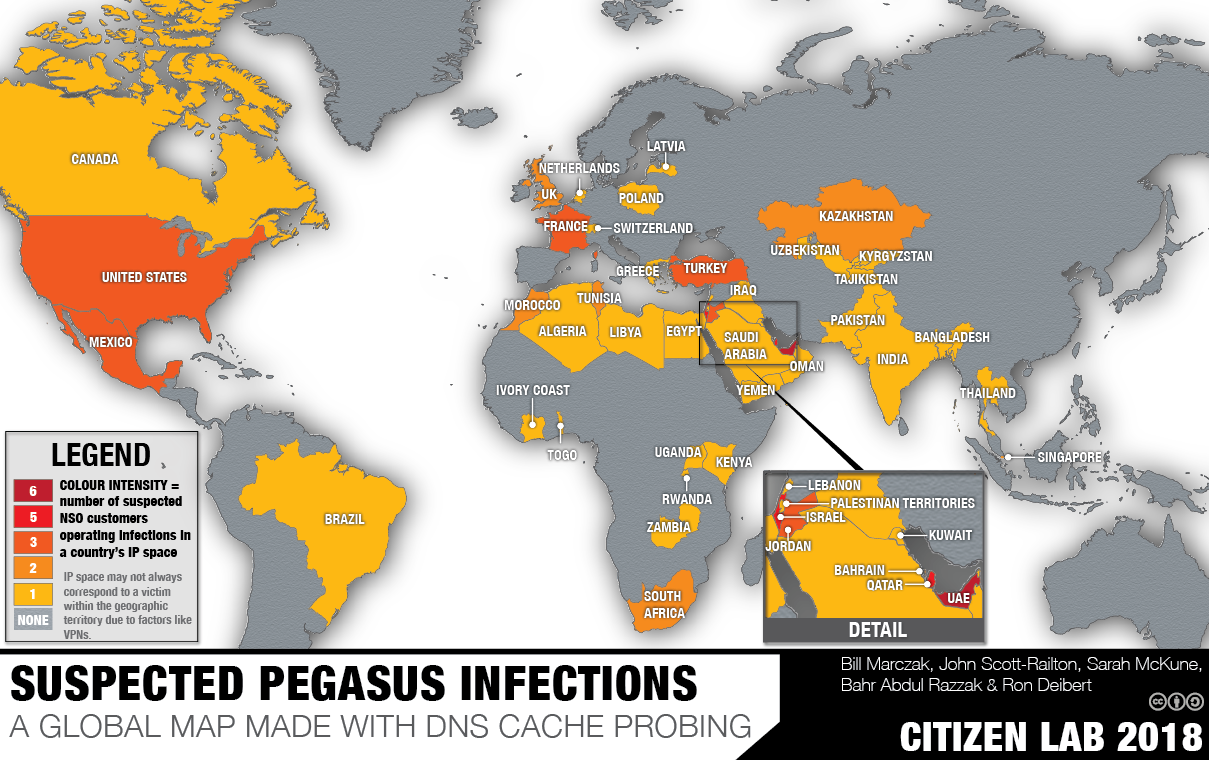
Our Hide and Seek investigation revealed an intriguing suspected infection in Quebec, Canada. We observed the infection moving between a consumer ISP and a university ISP, during the evenings and outside of the academic year. We linked this infection to an operator that we call KINGDOM, which was also responsible for the 2018 targeting of Saudi dissident Yahya Assiri and an Amnesty International researcher. Suspecting that the Canadian target was a Saudi-linked individual in Quebec, we contacted local members of the Saudi diaspora and attempted to identify a person whose movements fit the infection’s pattern. We found one match: Omar Abdulaziz, a university student with a regular pattern of evening activity. On two specific days, we were able to match the timing of his evening activity, and then his return home, to the movement of the infection between the two ISPs. We also examined Abdulaziz’s phone and found a fake package tracking notification SMS containing a Pegasus exploit link. These factors lead us to conclude with high confidence that Abdulaziz’s iPhone was infected with NSO Group’s Pegasus spyware.
Abdulaziz is a Canadian permanent resident and vocal critic of the Saudi government. In 2014, he was forced to seek asylum in Canada in the face of strong pressure from the Saudi government. Today, Abdulaziz is a university student in Quebec, where he continues to be an outspoken voice on human rights issues in Saudi Arabia. In August 2018, Saudi authorities threatened his brother with jail time in what Abdulaziz believes was an attempt to pressure him into silence. When he continued speaking out, two of his brothers and several of his friends in Saudi Arabia disappeared. Pegasus would have allowed the operators to copy Abdulaziz’s contacts, private family photos, text messages, and live voice calls from popular mobile messaging apps. The operators could have even activated his phone’s camera and microphone to capture activity, such as conversations, taking place in his home.
We are unaware of any legal authorization for the hacking and monitoring of Omar Abdulaziz in Canada by a foreign government. These actions may be contrary to multiple Criminal Code provisions, including willfully intercepting private communications, an indictable offence under section 184.
2. Omar Abdulaziz Targeted with Pegasus
Omar Abdulaziz is a prominent Saudi political activist who has been based in Canada since 2009. As a student at McGill University, Abdulaziz started a popular satirical news show on YouTube (Figure 3), which is highly critical of the Saudi government’s repressive tactics and human rights record. The show has garnered millions of views, and he has developed a large social media following. After the Saudi government withdrew his scholarship to study in Canada, Abdulaziz applied for asylum and was granted permanent resident status in Canada in 2014.
Abdulaziz continues to be outspoken about the Saudi government’s human rights record and has been particularly vocal and active during an ongoing diplomatic dispute between Canada and Saudi Arabia (See section 5), helping fellow Saudi students impacted by the dispute to claim asylum in Canada. Abdulaziz regularly appears in Canadian media, including a recent guest appearance on the Canadian Broadcasting Corporation (CBC)’s current affairs show, The Current, on August 10, 2018, where he said that Saudi authorities had entered his brother’s home in Saudi Arabia and “asked him to convince me [to] stop tweeting about what’s really going on between Canada and Saudi Arabia, or they’re going to send him to jail.” The Saudi government appears to have made good on the threat: later in August, Abdulaziz’s two brothers and a number of friends were arrested in Saudi Arabia. He believes that the arrests were an attempt to discourage him from speaking out further.
On a summer morning in 2018, Abdulaziz made a purchase on the online shopping website Amazon. Later that day he received a text message (Figure 4) purporting be a package shipment notification from the logistics company DHL. The URL in the message was from the domain sunday-deals[.]com. This domain belongs to a cluster that we previously identified as Pegasus exploit domains. Based on our prior research, we have high confidence that clicking on the link would result in the infection of the device with NSO’s Pegasus spyware. Abdulaziz, who says he uses a separate phone for his activism, told us that the message arrived on his personal phone. Abdulaziz recalled thinking that the message was related to his online shopping.
We first contacted and obtained the SMS (Figure 4) from Abdulaziz following an extensive global study of suspected Pegasus infections (Section 3), which identified an interesting Saudi-linked infection in Quebec.
3. DNS Cache Probing Leads us to Abdulaziz
On September 18, 2018, we published a report titled Hide and Seek, which describes how we scanned the Internet to generate a list of Pegasus spyware servers, used a technique that we call Athena to group the servers into 36 distinct Pegasus systems, and performed DNS cache probing of ISPs to identify locations from where suspected Pegasus infections were phoning home. In total, we identified 120 ISPs in 45 countries with likely infections (Figure 1) and 10 Pegasus systems whose operators were engaging in suspected cross-border monitoring (i.e., monitoring infected devices in more than one country).
[… con’d]
Spyware vendor defends hacking journalists, continues to embolden abusive governments
Camille Fassett
Reporter
March 26, 2019
CitizenLab
The Citizen Lab
The founder of of spyware vendor NSO Group appeared to defend targeting journalists, activists, and human rights defenders with its malicious software Pegasus in an interview days ago with CBS.
NSO Group has been back in the headlines again when it was uncovered that the wife of a murdered Mexican journalist was targeted with the company’s spyware after her husband’s assassination. What’s more, a Saudi dissident alleged in a December 2018 lawsuit that Pegasus was used in an attempt to spy on journalist Jamal Khashoggi before he was murdered by the Saudi Arabia government, a claim which CBS’s 60 Minutes explored on Sunday.
What is clear is that Pegasus, supposedly intended for government use only against “terrorists,” has been used against people who may pose headaches for their governments. NSO Group has failed to cut off relationships with authoritarian governments found to have targeted their critics, and it’s seems from CBS’s interview that NSO’s leadership has no intention to do so.
Used against journalists by their own governments
In 2016, Mexican journalist Sebastián Barragán received a text message that read: “I have credible evidence against public servants”. Beneath it was a link that researchers would later determine contained malware to remotely take over the device.
Citizen Lab, a technical lab and digital rights organization based in Toronto, has been researching Pegasus — malware used to hack people’s phones — for years. It has found that Barragán is one of an unknown number of media workers targeted with malware by their own government. Others include investigative journalist Carmen Aristegui and her son, Mexican journalist Rafael Cabrera, and Televisa anchor Carlos Loret de Mola. And due to the secret nature of spyware, it’s possible there are numerous other members of the Mexican press yet to be identified who have been targeted.
Compromising a journalist’s mobile device could threaten their sensitive reporting processes, privacy, and families. It can put sources and whistleblowers in serious danger.
What is Pegasus and how does it work?
Journalists — especially those covering sensitive subjects like corruption or national security — frequently receive messages, email attachments, and documents that promise to contain tips and useful reporting materials. Pegasus works by exploiting journalists who are doing their jobs following through on potential news or messages that appear to come from whistleblowers. Once a user clicks on a malware infected attachment, Pegasus can take over a device, essentially letting an attacker see everything that is happening on a phone.
Freedom of the Press Foundation Director of Newsroom Security Harlo Holmes said that a device becoming infected usually starts with a link received over SMS, or even through an end-to-end encrypted messaging service like WhatsApp.
“The language is crafted to lure a journalist specifically, by mentioning personal details or by sending them at times that are contextually appropriate, like in response to a real life incident. These tactics maximize the chance that the journalist will actually click through.”
“Modern software is incredibly complex, and sometimes bugs go undiscovered by their developers,” said David Huerta, a digital security trainer at Freedom of the Press Foundation. “Some bugs can break a device’s security safeguards. Companies like NSO Group find these security-breaking bugs and turn them into weapons.”
(For a more technical explanation of Pegasus’ pathology, see Citizen Lab’s reports.)
What can journalists do to protect themselves from spyware?
Malware like Pegasus can run in the background, and it’s possible journalists could remain unaware that their devices have been compromised and are being remotely controlled once they’ve clicked on an inflected attachment. Holmes emphasized that this is by design. “It’s made to be as stealthy as possible, and there are other factors that are dependent on the individual device that could make it very difficult for someone without a forensic background to know definitively.”
Journalists can minimize their risk of infection by malware through basic digital security hygiene, and, in particular, installing software updates.
“Pegasus works by taking advantage of security holes in your mobile device,” said Digital Security Trainer Olivia Martin. “The only way to patch these vulnerabilities is by applying system updates, which often contain security fixes.”
If journalists or activists suspect their devices have already been compromised, numerous digital rights and press freedom groups may be able to help or facilitate a connection to someone who can, including Freedom of the Press Foundation, Electronic Frontier Foundation, Committee to Protect Journalists, CitizenLab, and Reporters without Borders.
While no digital security practices are infallible, there are numerous resources are available for journalists to proactively protect their devices and sensitive reporting materials to minimize risks of malware infection before it happens. Check out Freedom of the Press Foundation’s digital security guides, and the Electronic Frontier Foundation’s surveillance self-defense kit.
“That’s a decision intelligence agencies should get…”
In an interview with CBS’ 60 Minutes on Mar. 24, NSO Group CEO Shalev Hulio and co-president Tami Shachar were presented with an opportunity to categorically denounce the unconscionable use of Pegasus against targets such as journalists.
Shachar disputed whether many of these abuses had ever occurred at all. “Nothing has been proven,” Shachar told CBS when asked about them, despite Citizen Lab’s public research showing that Pegasus has been used against journalists and human rights defenders.
When confronted with the reports that NSO Group sold Pegasus to Saudi Arabia in connection with the murder of Jamal Khashoggi, Hulio refused to “talk about specific customer." When asked to clarify whether he would not sell Pegasus to a country known for human rights and press freedom abuses, he only reiterated that Pegasus is sold to “prevent crime and terror.”
But governments like Saudi Arabia are quick label dissidents and free speech advocates as terrorists, too. While he claimed there were “a hundred” governments they wouldn’t sell to, apparently Saudi Arabia—one of the most repressive regimes in the world—wasn’t on that alleged “do not sell” list.
“They consider anybody who is a threat to their regime is a terrorist,” Saudi comic Ghanem Almasarir, who was also allegedly targeted by the Saudi government using Pegasus told CBS.
And perhaps most disturbingly, Hulio appeared to justify government targeting of journalists in the process of stopping “terrorism.” “...[I]f [journalists] are in touch with a drug lord… and in order to catch them, you need to intercept them, that’s a decision intelligence agencies should get.”
NSO Group’s answers show that the company has no intention of taking responsibility for its technology, breaking off its relationships with abusive governments, or categorically preventing the use of Pegasus spyware against journalists and activists. Companies like NSO Group continue to empower authoritarian governments to hack their critics, and in doing so, put countless journalists at severe risk.
https://freedom.press/news/spyware-vend ... vernments/




