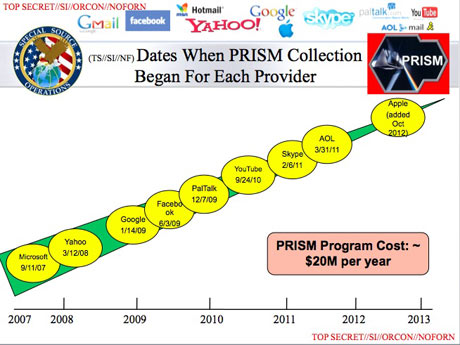
Steve and Leo examine the operation and technology behind the NSA's previously secret PRISM Internet surveillance program.Steve: Well, and it occurred to me that one of the reasons that he gave them to both outlets is because there was a prior instance where this kind of information was sat on for a year. And so that didn't - that wouldn't allow Edward to get the goal of getting this stuff disclosed. He says in the complete video, which I would commend people to watch, it's very interesting, that he does not want the story to be about him, to whatever degree possible. To some degree it is. He wants it to be about what's going on.
Okay, so with that little bit of sort of backgrounding, let's look at the James Clapper video. It's only 48 seconds. This is taken from the video record of congressional testimony that was open, obviously, to cameras exactly three months ago, on March 12th, where with prior notice of the question, the Director of National Intelligence was asked what the NSA is doing.
[Begin clip]
GEORGE STEPHANOPOULOS: ...is the desire for more public information. Now, he believes that the administration has not been misleading generally the committee and the public. But I want to play an exchange that was in the Intelligence Committee in March when James Clapper was questioned by your colleague, Senator Wyden.
[Begin embedded clip]
SEN. RON WYDEN: Does the NSA collect any type of data at all on millions or hundreds of millions of Americans?
JAMES CLAPPER: No, sir.
SEN. WYDEN: It does not.
JAMES CLAPPER: Not wittingly. There are cases where they could inadvertently perhaps collect, but not wittingly.
[End clip]
Leo: All right.
Steve: So there it is. That's our...
Leo: That's not even a non-denial denial. That's a denial.
Steve: [Laughing] There's no way.
Leo: There's no way.
Steve: There's no way to walk yourself out of that one.
Leo: Yeah.
Steve: And, I mean, and then Andrea Mitchell interviewed him for "Meet the Press" on Sunday. And I'm looking for where it was he - he actually said to her, "I thought, though in retrospect, I was asked a 'when are you going to ... stop beating your wife' kind of question, which is ... not answerable necessarily by a simple yes or no." So this is - he said to Andrea, "So I responded in what I thought was the most truthful, or least untruthful, manner by saying, 'No.'"
Leo: Okay.
Steve: Oh, I know. It's just painful.
Leo: Okay.
Steve: I know. There's a great - if anyone's curious, there's a great take on this. Fred Kaplan wrote an article in Slate.com, and it says, "Fire DNI James Clapper. He lied to Congress about NSA surveillance." And I don't know whether the guy has to go, but he certainly did lie because we now know much more than we did three months ago when this was said to - when he was asked this openly. And the EFF, of course, the Electronic Frontier Foundation, is all over this, happily, or I'm happy to say. I really thought that their summation of this was perfect.
They said, quoting from a longer article, they said: "All of this would be amusing if the administration's main argument to defend the NSA's massive spying program" - and "spying" is their word, not mine. Certainly it is surveillance. Spying requires a judgment. "All of this would be amusing if the administration's main argument to defend the NSA's massive spying program is that Congress has been informed of all their activities. Democracy can't function when Congress is 'informed' by the 'least untruthful' statements of the administration, using unusual definitions that are designed to given an impression that is the polar opposite of the truth."
I skipped part of this that explains, when he responded this way, Andrea said, well, but how can you answer no, that you're not collecting information? And then he said, "Clapper's deceptions don't" - I'm quoting from the Slate article. "Rambling on in his rationalization to Andrea Mitchell, he focused on Wyden's use of the word 'collect,' as in, 'Did the NSA collect any type of data ... on millions of Americans?' Clapper told Mitchell that he envisioned a vast library of books containing vast amounts..."
Leo: Oh, please.
Steve: "...of data on every American. 'To me,' he said, 'collection of U.S. persons' data would mean taking the book off the shelf and opening it up and reading it.'"
Leo: But this is interesting because all of these things he's saying really are an acknowledgment that "no" was a lie.
Steve: Yes.
Leo: It's only not a lie if you have these bizarre interpretations of what the question meant.
Steve: Well, yeah, I mean, what can he say now with this recording of him three months ago flatly denying what we now know has been true for years?
Leo: Right.
Steve: Okay. So, first, what was authorized under the FISA Article 215, that's the telephony metadata collection. What I found interesting about it was essentially what's going in is that all the telephone companies naturally keep the records that they need for billing. So they're recording so-called "metadata." We've talked about metadata. Metadata is essentially sort of the, not the main content, it's the embellishment. For example, when we talk about a browser query, there's the query, and then there's the headers, and the headers are metadata. They're additional information. Date and time stamp and cookies and so forth are browser metadata. Or in a file system, you know, you're storing files, but it's also keeping track of when you last accessed the file and when it was modified and when it was created and file privileges for example, who's able to access it. That's metadata.
So similarly, telephony metadata is - it's like where you are by, like, which cell tower your call is coming in on; your originating phone number, or actually it's the serial number of your phone; the number you dialed; probably where it is maybe, though if it went off out into a different phone system, they may not have that. But basically it's your call records. It's not your conversation, it's the event features of the call.
Well, what's interesting is that phone companies have no need to retain that in perpetuity. They typically only keep it for 60 to 90 days. So what's happened is, as authorized under this Article 215, the NSA has set up arrangements with all of the domestic phone companies to acquire this data before they delete it. So, and it turns out that it's not against the law to do this. The so-called "business records" have been ruled by the Supreme Court not to be subject to privacy protection. So if AT&T or Verizon's business records, this is just their records for their own purposes, and...
Leo: This is like the billing, the billing information that they would have.
Steve: Yes, exactly. And it's about to be deleted, and the NSA says, oh, oh, oh, hold on a second, let us make a copy of that. Or just send it to us before you hit delete. So in listening to all of the buzz about this, there's this downplaying of, well, but it's not your conversations. It's just the metadata. And I'm sitting here thinking, oh, my god, I mean, do you realize what it means? If there is a facility huge enough to capture and contain all of that, and the computing resources necessary to link it together, what this builds is an incredible graph of all of the connectivity that exists between everybody with a phone in the United States.
And it's funny because in my notes I was already making a note that, well, the history is also really important, and crucially important to the NSA because, for example, if they got, identified a person who was a suspect of something, a terrorist presumably, or a bad guy qualifying for further surveillance, they can query this network. And what the continual collection of the data means is that they can go back in time, they have a time machine that allows them to walk back and look at the history of all past connections over time. That's unbelievably rich. And it happened that Edward, during his interview, said exactly that. So I thought, it's a very short piece, we'd just hear it in his own words.
[Begin clip]
EDWARD SNOWDEN: ...care about surveillance. Because even if you're not doing anything wrong, you're being watched and recorded. And the storage capability of these systems increases every year consistently by orders of magnitude to where it's getting to the point you don't have to have done anything wrong. You simply have to eventually fall under suspicion from somebody, even by a wrong call. And then they can use this system to go back in time and scrutinize every decision you've ever made, every friend you've ever discussed something with, and attack you on that basis to sort of derive suspicion from an innocent life and paint anyone in the context of a wrongdoer.
[End clip]
Steve: So...
Leo: And by the way, I want to point out that, if anybody would say, well, the government would never do that, just there are some pretty good examples with Nixon's enemy list and J. Edgar Hoover's persecution of Martin Luther King.
Steve: Yes.
Leo: That it is not unusual for our government, our republic to do this kind of thing.
Steve: And it doesn't, I mean, these are people who at the time righteously believed that they were doing the right thing. I mean, they were doing it in secret, and that's a problem. And, I mean, secrecy is what we have to worry about because, exactly as you say, Leo, there is ample history of abuses of this kind of data collection. And so I just wanted to shine a little light on this notion that, oh, well, telephony metadata is not useful. Remember we talked about some time ago this new facility that the NSA is building. We were scratching our heads at the time, wondering what is a zettabyte, because this place can store five of them. Five zettabytes worth of...
Leo: Million square feet. Million and a half square feet.
Steve: Yes. It's a million and a half square feet costing $1.2 billion dollars, 26 miles south of Salt Lake City, in a town called Bluffdale, Utah. It uses 65 megawatts of power. It has its own power substation and, like, cooling ponds; and, I mean, it's just phenomenal. And at the time we were thinking, well, what are they going to put in that? What are they going to fill that with? Well, you know, we have an answer to that question now.
Leo: We continue on. Steve Gibson, we're talking about, of course, PRISM and the revelations which continue from the Guardian and The Washington Post and others, about some sort of federal spying. We've heard the word "Echelon" for more than a decade. We knew that after 9/11 President Bush authorized warrantless wiretaps. I remember, don't you remember, the whistleblower that in 2000, I think '6 or '7, told us that the NSA had a secret room at AT&T headquarters in San Francisco so that they could collect this kind of data. So this is not - we're not talking about anything new here.
Steve: No. And I think that, well, there is something new. And that's PRISM. And I'm going to explain what's been done differently than as far as we know anything we had before.
Leo: Excellent.
Steve: Because this may be, this podcast may be viewed by people who are not regular listeners, if people want to send this link to others and so forth, I'm going to give a little bit more background to the way the Internet works than our regular listeners would need. We've had a series of podcasts in the past famously on how the Internet works. And of course I'll keep it brief and aim it at the point that I'm bringing.
So what we have with the Internet, the word "Internet" is interconnected networks. The Internet itself is a global interconnection of privately owned networks. And in some cases they may be government-owned networks. Or, in the U.S., generally we have AT&T and Verizon and Level 3 and large carriers who then supply connectivity to Cox Cable and Cablevision and smaller carriers, and ultimately down connected to our own little network in our homes. And this is all glued together with routers. We've got consumer routers made of plastic in our homes; but there are, as they're called, Big Iron routers, which route vast quantities of data across the Internet.
And I'll just take Google as an example because it's so well known. All over the world, people are sending data to Google. They're putting Google in their browser. They're asking Google to find them things. They're doing searches. Maybe they're using Gmail and establishing a secure connection to a Google server that exists in a Google datacenter somewhere on the planet. So the way that happens is that, with all the people scattered around, they put packets of data onto their own network, the network that they're on, and the router on that network by definition is connected to at least two places. Consumer routers are connected to their home network and to their ISP's network. So there's only two connections.
But the router's job is to forward that data towards its destination. So when someone at home puts a packet of data bound for Google, it goes to their router, and the router sends it to the ISP. The ISP's network looks at the packet's addressing and says, oh, okay, it goes to an ISP router. Now, a big ISP router will have an octopus of connections. It'll be connected to many other routers, not just one other network, many other networks. And so it uses its routing tables to send the packet towards Google.
And this is where the robustness and the strength of the Internet comes from is it's inherently redundant. There are many routes to get to Google from any given place. But there's typically a best one, and so the router will try to use that. If that link happened to be down at the moment, the router would go, oh, and use a next-best route, maybe off in another direction that would then loop back around and eventually get there. So that's how this works. It's an interconnected set of networks that are connected to each other. That is, the interconnection points, you think of sort of like a spider web where the points that the web comes together there's a router there. And the router isn't very smart. It knows just enough to route that data in the proper direction.
Now, there's an interesting phenomenon that occurs, which is, as you get closer to Google, more of the traffic which is being carried by routers will be Google's, as a percentage. If you think about it. Because the Yahoo! traffic, that went off in a different direction. And the Microsoft traffic was headed to Redmond, and the Apple traffic was to Apple's farm, their datacenter in Cupertino or wherever. So the idea is that, with each of these hops, as they're called, across the Internet, the packet is getting closer to its destination. And if you think about it, the percentage of traffic that that router is carrying or forwarding will tend to be concentrated toward, for example, its destination, Google. There will be no Yahoo! traffic if Yahoo!'s routers and their datacenter is off in a different direction. That will have been sent out other links. So there's a concentrating phenomenon.
And the other thing that's interesting is then to ask yourself about the question of ownership. Who owns this data? And again, I don't know, from a legal standpoint. I'm coming from a technology standpoint. But this is still the public Internet. It was the public Internet when it was on your ISP, I mean, it was their network. But the way this all works globally is everybody with connected networks has agreed to provide transit for, to carry everybody else's traffic. So they just said, okay, I'll carry yours, if you'll carry mine. And that's the way the Internet works.
But the packet that a user generated is just this little blob of bits that has an address, a source and a destination IP, the Internet protocol address that is used to send it towards its destination. And so the wires that the packets are moving over belong to the public or private carriers of the data. But the data is sort of - it's public. I mean, you've lost control of it. You've put it on the Internet, and it's gone. So, well, we'll come back to this because it's an interesting question about what this means that what I think it's very clear the NSA has done.
Now, as Leo mentioned a minute ago, back in '07 there was a lawsuit, and I have not had any chance to do any deep research on the lawsuit because it really wasn't relevant to this. But it was about, I think, some privacy complaint that someone had. Testimony was given in deposition of a technician who worked in a facility at 611 Folsom in San Francisco. And Leo, I provided a link to a PDF to you. If you put up the image there, that's useful. I'm just going to read what the EFF's page has. They summarized this, and it is - it's another piece of this puzzle [www.eff.org/NSA-spying].
Leo: This was, by the way, another whistleblower.
Steve: Yes.
Leo: So unfortunately, this is what often has to happen is somebody has to step forward, say I have knowledge of this. This is an employee, I think, of AT&T.
Steve: Yes. And in fact, a few seconds ago, while you were telling people about proXPN, I tweeted five bit.ly links to a set of documents, including the redacted testimony for national security reasons that this comes from [bit.ly/sn408a, bit.ly/sn408b, bit.ly/sn408c, bit.ly/sn408x, bit.ly/sn408y]. So the full testimony is available with photos of the door of the room I'm going to be talking about in a second.
Leo: Amazing.
Steve: "AT&T's Internet traffic" - I'm reading now from the EFF's summary of this. And this is titled "AT&T's Role in Dragnet Surveillance of Millions of Its Customers: AT&T's Internet traffic in San Francisco runs through fiber-optic cables at an AT&T facility located at 611 Folsom Street in San Francisco. Using a device called a 'splitter,' a complete copy of the Internet traffic that AT&T receives - email, web browsing requests, and other electronic communications sent to or from the customers of AT&T's WorldNet Internet service from people who use another Internet service provider - is diverted onto a separate fiber-optic cable which is connected to a room, known as the SG-3 room, which is controlled by the NSA."
Leo: By the way, this is not cellular data. This is not phone calls. This is ATT as an ISP.
Steve: They - yes.
Leo: It's important because the ISP is the - you mentioned collection point. The ISP is the collection point for everybody. Everything you do goes through that ISP.
Steve: Yes. And the way the Internet is organized in a hierarchy is we have so-called Tier 1 providers like Level 3, like Deutsche Telekom, like AT&T, the really big carriers like Sprint. These are - and there's, like, I think there's a small number, 20, maybe it's 12 or 25. I can't remember the number exactly. But there's a relatively few. And they're sort of the - they're the networks that straddle the globe; or, for example, maybe an entire country. And then they resell connections to their network. They resell bandwidth to Tier 2 providers, then to Tier 3 providers in a hierarchy. So what this is, this is a fiber-optic tap using a splitter in the Folsom building in San Francisco that makes a copy of, essentially receives a copy of all the data passing along this major trunk of AT&T. And it goes into this SG-3 room which, as EFF writes, "is controlled by the NSA. The other copy of the traffic continues onto the Internet to its destination."
Continuing to read from the EFF document: "The SG-3 room was created under the supervision of the NSA and contains powerful computer equipment connecting to separate networks. This equipment is designed to analyze communications at high speed and can be programmed to review and select out the contents and traffic patterns of communications according to user-defined rules. Only personnel with NSA clearances - people assisting or acting on behalf of the NSA - have access to this room.
"AT&T's deployment of NSA-controlled surveillance capability apparently involves considerably more locations than would be required to catch only international traffic. The evidence of the San Francisco room is consistent with an overall national AT&T deployment to from 15 to 20 similar sites, possibly more. This implies that a substantial fraction, probably well over half, of AT&T's purely domestic traffic was diverted to the NSA. At the same time, the equipment in this room is well suited to the capture and analysis of large volumes of data for purposes of surveillance."
Now, this came from sworn testimony by Mark Klein, which he gave under oath on the 26th of May, 2006, so a few years back. And this is lengthy, I'm not going to go over it, but there are a few points I want - I'll just give you a sense for it. He says, "I, Mark Klein, declare under penalty of perjury that the following is true and correct: I am submitting this declaration in support of Plaintiff's Motion for a Preliminary Injunction. I have personal knowledge of the facts stated herein, unless stated on information and belief, and if called upon to testify to those facts I could and would competently do so. For over 22 years I worked as a technician for AT&T Corporation, first in New York and then in California. I started working for AT&T in November 1981 as a Communications Technician." Okay, and blah, blah, blah.
So he's been put in - he became involved in the installation of this room that we were just reading about. It says: "AT&T Corp., now a subsidiary of AT&T Inc., maintains domestic telecommunications facilities over which millions of Americans' telephone and Internet communications pass every day. These facilities allow for the transmission of interstate or foreign electronic voice and data communications with the aid of wire, fiber-optic cable, or other like connections between the point of origin and the point of reception."
He says: "Between 1998 and 2003 I worked in an AT&T office located on [and then it's been redacted] in [redacted] as one of [redacted] computer network associates in the office. The site manager was a management level technician with a title of [that's redacted], hereinafter referred to as FSS #1. Two other FSS people [blah blah blah]." He says: "During my service at the [redacted] facility, the office provided WorldNet Internet service, international and domestic Voice over IP," so forth and so forth.
I'm going to skip down, and he says: "In January 2003, I, along with others, toured the AT&T central office on Folsom Street in San Francisco, actually three floors of an SBC building. There I saw a new room being built adjacent to the 4ESS switch room where the public's phone calls are routed. I learned that the person whom the NSA interviewed for the secret job was the person working to install equipment in this room. The regular technician workforce was not allowed in the room.
"In San Francisco the 'secret room' is Room 641A at 611 Folsom Street, the site of a large SBC phone building, three floors of which are occupied by AT&T. High-speed fiber-optic circuits come in on the eighth floor and run down to the seventh floor, where they connect to routers for AT&T's WorldNet service, part of the latter's vital 'Common Backbone.' In order to snoop on these circuits, a special cabinet was installed and cabled to the secret room on the sixth floor to monitor the information going through the circuits. The location code of the cabinet is [and he gives a number] which denotes the seventh floor, aisle 177, and bay 04.
"The secret room itself is roughly 24x48 feet, containing perhaps a dozen cabinets including such equipment as Sun servers and two Juniper routers, plus an industrial-size air conditioner. Plans for the secret room were fully drawn up by December 2002, curiously only four months after DARPA started awarding contracts for TIA," whatever that is [Total Information Awareness]. And then we have two photos in this deposition, photos showing the room.
And then he says: "While doing my job, I learned fiber optic cables from the secret room were tapping into the WorldNet circuits by splitting off a portion of the light signal." And that's why the program is called PRISM, Leo. What does a prism do?
Leo: Oh, it splits a light signal.
Steve: It splits light. "I saw this in a design document available to me entitled 'Study Group 3, LGX/Splitter Wiring, San Francisco,' dated December 10th, 2002. I also saw design documents dated January 13th, 2004 and [blah blah blah] which instructed technicians on connecting some of the already in-service circuits to the 'splitter' cabinet, which diverts some of the light signal to the secret room. The circuits listed were the Peering Links, which connect WorldNet with other networks and hence the entire country, as well as the rest of the world."
So here is what NSA has done. This is installed in San Francisco. The NSA has installed this technology, this PRISM fiber-optic tapping/splitting technology, just upstream of all of those companies named. It is absolutely true that they probably never knew about it. They may be finding out about it for the first time, listening to this podcast. And I imagine it will suddenly all make sense to them. The NSA has said they had direct access to these companies' servers. Well, and that's the funny thing, the thing I noticed when I realized what was going on is that "server" is the only word anyone knows. My mom knows the word "server." Mika Brzezinski on "Morning Joe" knows about the AOL server or Google's servers. That's in the common parlance.
The word that we should have been using is "router." And that's not a word that people understand. But that's the key to this technology. As I was saying, routers concentrate data. Somewhere, and the NSA knows exactly where it is, Google is buying their bandwidth. And there are routers upstream of Google whose purpose it is to take the disparate packets all coming into Google and route them down fiber-optic lines which finally make the transit into Google's data center. It is unnecessary to have access to the datacenter if you are tapping the fiber-optic line going into and out of the datacenter.
Leo: Okay, but isn't this encrypted traffic?
Steve: Ah. Well, yes and no. So some of it is encrypted. But, for example, how is this useful? We all know that email has never been an encrypted technology. Email SMTP does not involve encryption when we send email from place to place unless an individual deliberately encrypts their email. And even if you were using Google, you may have a secured SSL connection to Google's web server when you're using Gmail. But the moment that email leaves to go to your mom on AOL, or it goes anywhere else outside of Google, it is being sent over SMTP connections which are not, that is, SMTP protocol, which is not encrypted. So even whereas our interchange with Google on their website is encrypted, email transiting the Internet isn't.
So all email outbound from Google is fully readable, and all email incoming to Google is fully readable. It's certainly true, and our surveillance state is unhappy with the growing use of encryption. But a huge, a vast, still the majority, arguably, of data is not encrypted. And then there is other sorts of metadata. We've talked about this on this podcast, for example, DNS queries. When you go to a website, your system has to query a DNS server in order to get the IP address. Well, that's typically not encrypted unless you use the service that OpenVPN offers.
So what we have is we have this system called PRISM. We have this bunch of companies that are absolutely sure that they have never agreed to blanket eavesdropping/wiretapping with the NSA. And I believe them. If the NSA had reason to specifically require data that is specific to a given case, we already know they go to a court, they get a warrant, and under a bond of secrecy they're able to get the data that the company has, if any, and the company is bound not to say it.
I don't believe that's what's going on. The fact that this is called PRISM, the fact that a prism splits light, the fact that we know from this prior testimony that there is a facility on Folsom that the NSA has been doing this - in fact, further on his testimony he quotes the specific routing technology, the gear that's being used. There is a semantic analysis technology. I don't know if I can find it here on the fly. But I just tweeted all the documents that contain this information for anybody who's wondering.
Anyway, I am convinced, from everything that I've seen, that - oh, also the timeline. This is not something you can do instantly. This is going to take time. So what it looks like from the timeline that we saw in one of those slides, where individual corporate entities were added to the PRISM project one at a time, that fits the facts, too. The idea that the NSA would say, okay, now we want to get everything, all of Apple's traffic we want to tap. Essentially what we have is wiretapping of these companies.
Now, remember that I don't know legally where this stands because this is the Internet. You could argue that, if somebody was installing, surreptitiously installing equipment inside Google's facility, well, then it's under Google's control, and it's Google's. All the NSA is doing is tapping the communications, which is still the Internet, it's just been filtered down so that it's nothing but Google's traffic.
Leo: So all they really need to do is find the backbones, the big Tier 1 providers. And you say there are about eight or nine of them? Or how many are there?
Steve: Well, no. What you need is, where you need to place the tap is as close to Google as you can get, or as close to Microsoft, or as close to Yahoo!, because you don't want a lot of other extraneous traffic. You want to get all of that.
Leo: I want it all.
Steve: Yes.
Leo: Okay. So would it have to be in Google's facility?
Steve: No. It would be - so, no. Google's going to have fiber that is going to be fed from their provider. Google is buying bandwidth from somebody.
Leo: Let's say it's Level 1. We don't know.
Steve: Level 3.
Leo: Or Level 3, I mean.
Steve: Yes.
Leo: Actually, let's say it's Level 1.
Steve: Okay, good.
Leo: Somebody called Level 1.
Steve: Somebody innocent.
Leo: So you would then go, as the NSA, to Level 1, issue them an NSL, a National Security Letter, which means they can't speak.
Steve: Yup.
Leo: And say we want to - we're just going to plug this little thing into your router. Can you give us a room?
Steve: Yes. We need, yes, we need a secret room, and we're going to staff it with our own people. Oh, at one point the air conditioning, the air conditioner's condensation tray overflowed and was spilling water in the secret room, and it was dripping down to the floor below, so that caused some problem. I guess they hadn't quite figured out how to drain the air conditioning condensate. But, yeah, so give us a secret room. So go ahead, Leo. I want you to restate it.
Leo: No, well, I think that you've answered my question. So they go to the Tier 1 provider, the Level 1 or whoever it is, and say give us...
Steve: Well, no, they go to the bandwidth provider of the company they're targeting. So it's not Tier 1. It might be Tier 3. I mean, it's like...
Leo: Aha.
Steve: Because it's going to come down the hierarchy until it gets to the entity they want to tap.
Leo: And you don't need to tell Google about this.
Steve: No. Google would have no idea.
Leo: And this gives them plausible deniability. They may know about it, but they may just - this gives them plausible deniability. No, no, they don't have access to our servers.
Steve: No, I think they'd be furious, Leo. They're being - this is a wiretap on...
Leo: Yeah, but surely they've figured this out.
Steve: Well, I haven't heard about it anywhere in the news. Nobody else seems to have figured out what PRISM is. And there is - this fits every fact. It's why it's called PRISM. They're using fiber-optic cable splitting. And it fits the whole timeline. They didn't just, bang, do it all at once because it's going to take time. They're going to have to go to the individual carriers who are providing bandwidth to these companies who are - and, I mean, the only thing Apple and Google and Yahoo! represent are major social focal points.
Leo: Right.
Steve: And actually, by tapping those major carriers, those major companies, the NSA is minimizing the work that they have to do because most people are going to use Google or Yahoo! or AOL and Apple and so forth.
Leo: There's precedent for this because remember Carnivore, which was renamed after they realized it was a terrible name, which was the FBI's attempt to get every Internet service provider in the country to put a box in their - again, another focal point. In fact, the best place to collect all this stuff is at the ISP level. And for individuals you can get it in every respect. And there's never really been any proof that this didn't happen. And then of course there's the recent law which was not passed, but might well still be, requiring ISPs to collect 18 months of data for use.
Steve: Well, so, again, I'm...
Leo: This all makes perfect sense. It's exactly how they're operating, and in fact the most efficient way to do it.
Steve: Yes. Yes. This is - if the NSA had come to me and said, Steve, what should we do?
Leo: How would I do this, yeah.
Steve: This is what I would design. I would design this system. I would say, you want to get, you know, if you need to be - you need to keep this a secret. You want to get all the traffic coming in and out of Google. You get as close to Google as you can. You get on the router that is feeding Google, and you clone all of the data. And that's exactly - and that's why it's called PRISM is that now, at this bandwidth level, they're using fiber optic cables, so it splits the light. The power drops by 50% down each of the splits because the power of the light has been split, but that's - there's still plenty. And so it's going to be received easily by the other end. And then it goes off to this secret room controlled by the NSA.
And it also fits what we heard because there was - we heard that there was this notion, I mean, we heard of PRISM, that you can - or maybe it was Edward who said that you could task this equipment to find things. So they're - so an analyst...
Leo: Wow, smarter than just a collector, it's actually sifting.
Steve: Yes, yes. And I'm looking here, if you see the link, it's klein-decl. It's cryptome.org/klein-decl.htm. So it's Klein Declaration. In there he shows the documents about installing the splitter, how to split it, all of the technical details. And he does cite the name of the company providing this - they call it "semantic analysis" equipment. So the idea is that an analyst sitting in Langley is able to task the Google tap to select, I mean, this is a torrential flood.
Leo: Remember, this was years ago, though. And I would guess now, because they have such high-end storage and processing, they probably just send it all to the center; right?
Steve: Well, they're readying five zettabytes.
Leo: Yeah, they'll end up sending it to Utah.
Steve: So why filter it? We may miss something we want.
Leo: Right. Well, precisely.
Steve: Let's just suck...
Leo: Save it all.
Steve: Yeah, suck it all in.
Leo: You never know what you might want.
Steve: Yup. And again, having the history allows them to go back and do research on the past.
Leo: So let me - let's get clear, though. What is it that they have? This is no longer metadata. This is all data that isn't encrypted.
Steve: Yes. So, yes. So, now, at this point, as far as we know, the use of SSL encryption will withstand the NSA's attack.
Leo: But they're saving it anyway, just in case.
Steve: Well, they're saving it because they know in the future your computers will get stronger. Maybe quantum computing technology will actually allow them to just collapse the 128-bit key. I'm uncomfortable with 128 bits. We really need to start thinking 256. And we'll talk about that soon on the podcast because the protocols exist on SSL; but, as we've spoken about the way SSL exists, both ends have to agree. And we've got all these banks out there who are scoring F's on their SSLLabs.com test because they're not using strong encryption. And so the cipher string has to be agreed to by each end.
But the point is certainly there's a percentage of data that the NSA - it is encrypted. They cannot read it. But any email coming into Google, any email leaving Google, which is to say any non-Gmail-to-Gmail communication, does exit - and in fact maybe it still goes, if it's going off to a different physical datacenter in Google, it's going to go out over the Internet. I don't know if Google maintains encryption of email traffic between their datacenters.
But anything, essentially everything coming and going in and out of the companies that were named, is probably now being tapped. And PRISM is the technology that does it. It is sitting just upstream of these companies, monitoring everything that they're doing, everything, I'm sorry, that every of their users are doing. Anything not encrypted is subject to surveillance.
Leo: Quite amazing. And what you say now makes perfect sense. I think you're right. We don't know because, A, anybody who knows probably is enjoined from saying anything by pretty strong federal restrictions.
Steve: Right. It's the only reason I can talk about it is that no one there told me anything, yes.
Leo: But what does make sense and I think is interesting is this is probably too technical for most lay observers to deduce. So they say "have full access to servers." And while Google is certainly, you know, the engineers at Google are certainly smart enough to understand that this is the risk, they're not allowed to say anything anyway. So they're going to say only what's strictly, you know, that they're allowed to say that's strictly true, which is they don't have access to our servers.
Steve: Yes. And it's absolutely true. They do not. Unfortunately, they have access to the pipe connecting your servers to the rest of the world.
Leo: They don't need access to your servers.
Steve: Yes, exactly. And it's funny, too, because the press, in trying to explain this discontinuity between the formal statements that were immediately issued by these companies, they were saying, well, they're parsing their words very carefully, or they've got really good attorneys. It's like, no. They're absolutely not complicit in this. The NSA has installed a tap in their connection to the Internet. And the tap, I'll say again, it's on the Internet. I mean, I don't know about the legality of this, but I was chuckling to myself because the NSA is doing this deliberately. Google did it by mistake when they were collecting unencrypted WiFi with their mapping technology.
Leo: Right, right. Well, so if you want to explain this to your grandma or a layperson, it's really something that I think any layperson can understand. You just say it's an upstream tap.
Steve: Yes.
Leo: They're tapping the Internet, and as a result they're getting...
Steve: Where it connects to the company.
Leo: To these companies.
Steve: Yeah.
Leo: And for all we know they're also tapping it where you connect to the Internet. So they can get you coming and going if they want.
Steve: Well, yes. They would, see, again, being sympathetic to the need for intelligence, I get it that they chose these companies because they are major focal points. So a tap located there would give them the most bang for the buck.
Leo: And the reason we know these companies is this is one of the slides in that slide deck that Snowden released.
Steve: Yes.
Leo: However, I have to think that really it goes much wider than this because, if you're going to Level 1, you might as well just say who else connects through you?
Steve: Well, Leo, we already know because the article that I read was an AT&T facility. This was tapping the so-called backbone. This is the - remember that the way these - at the very, very top we have the so-called Tier 1 providers. And they have what's called peering relationships with, like, so, like Level 3 and AT&T and Sprint have peering relationships with each other, where they are, because they're peers, and so they agree that they will send traffic to each other. What we read in this testimony and on this EFF page is this was the peering pipe at AT&T going to its peers.
Leo: So they did it. This is how they did it.
Steve: Yes. This is the entire Internet being tapped.
Leo: Yeah. If you were a WorldNet user in 2007, they were listening.
Steve: Yeah. Or, if you happen to be at two distant locations, and your traffic goes through AT&T on its way to another network, then it's present there. And I just - there's one more comment I wanted to make that I thought was - I felt, I mean, I understood it, and that is that Europe is very unhappy over this. We're sitting here, and the NSA is saying, and I don't believe them because how can I believe them now, they're saying we're only, I mean...
Leo: No, that's obviously not...
Steve: I mean, their great caveat is that they're only looking at foreign people.
Leo: Well, that's all they're technically allowed to look at.
Steve: Well, and that's nonsense.
Leo: By their charter, yeah.
Steve: Yes, that's nonsense. But even so, that means they're looking at everything outside the U.S. Well, that's half of this podcast's listeners, Leo.
Leo: And the FBI has the charter to do inside the U.S. and is presumably doing this with the help of the NSA.
Steve: Well, and I saw a little blurb yesterday that said that the "Finnish communications minister, Pia Viitanen, has stated bluntly that the NSA may be breaking the laws of Finland. According to the Finnish Constitution, capturing and reading emails or text messages without privileges is illegal."
Leo: I think it's illegal in the U.S.
Steve: "Viitanen plans to take up the issue with the European Commission."
Leo: Wow.
Steve: "Several European countries are apparently considering unleashing Neelie Kroes..."
Leo: Oh, she's great.
Steve: "...the feared European Commissioner for Digital Agenda, in an effort to fight back against the NSA's PRISM program."
Leo: Don't mess with Kroes, that's for sure.
Steve: So hide under a desk.
Leo: Oh, wow. The mind reels.
Steve: And lastly...
Leo: Yes, go ahead.
Steve: Lastly, in reaction to this, a site has been put up that immediately, along with the EFF - stopwatching.us. Stop Watching Us. It's taking signups. There are 63 companies that have already, or organizations that are behind this. And so I suggest that anybody who's interested - they've got a really crappy security certificate. I was disappointed in the security certificate for the site because it's an HTTPS site. I would like to see something better there. But stopwatching.us is someplace that anyone can go who's interested.
And Jon Stewart is off for the summer directing a movie, so John Oliver is standing in for "The Daily Show" on Comedy Central. His opening piece Monday night [June 10, 2013] was wonderful. Basically summed up the political side of this with the typical "Daily Show" comedy. So I wanted to recommend that to our listeners. It was really terrific. So if you can find "The Daily Show" for Monday, which would have been, what, the 10th of June, the beginning of it with John Oliver as the guest host, filling in for Jon Stewart, was great.
And, yes, Leo, you're right, the mind reels. But at least now we know what's going on.
Leo: The next step I would like, and maybe we'll do this on Know How, maybe you can do it, too, is telling people some simple steps you can take to encrypt your email, encrypt your traffic. If you really, I mean, you can't hide who you're sending it to because that has to be public, otherwise it won't get there, although I guess you could use Hushmail or something like that and have private addresses, as well. But I think this, you know, for a long time I used PGP and encouraged people to send me encrypted email. Nobody ever did it.
Steve: Here's what's interesting is the polls came out yesterday morning.
Leo: 56% of Americans don't care.
Steve: I saw 62, 62 versus 34% of Americans say they are okay with this.
Leo: Because it's protecting us against terrorism.
Steve: If it protects us against terrorism.
Leo: Right.
Steve: And then there's always the conundrum, well, if you don't have anything to hide, what do you care?
Leo: I even heard a federal official say that this week, that nobody who's a law-abiding citizen should worry about this.
Steve: So I was very annoyed that Google got in the trouble they did for inadvertently collecting unencrypted WiFi which was being broadcast to them in the air, when here we have the NSA that has used prisms to split the optical cables going to these major companies to install local taps. It's just there's something wrong there. I understand the NSA's need for the data, but - in order to find bad guys. But they have to tell the truth. I mean, they have to tell Congress the truth. They don't have to tell me or you. They have to tell Congress because that's the only way that we have checks and balances.
Leo: Well, and they may. They may have told the House Foreign Intelligence, and they may have told people this. It's my suspicion that some lawmakers, not all, know about it and have approved it. And I think this is the problem is that people want to be safe against terrorism and understand that this has to be done. And I think the fear is, if the federal government admits to this, then the bad guys go, oh, well, that's no problem, we'll just use Cryptocat.
Steve: Well, here's what's really interesting, too, is imagine that you have the dragnet over all phone communications, all telephony metadata. And three clever terrorists say, oh, well, we're going to avoid the system. We're going to get so-called "burner" phones, you know, temporary phones. And we're never going to give the phone number out. We're never going to dial any other phone except these three. And we're only going to use it to talk to each other. Well, how suspicious is that?
Leo: You immediately know.
Steve: Yes.
Leo: Big red flag.
Steve: The NSA would find three little nodes with lots of connections among themselves, but nobody ever phoned into them, and they never phoned out to anyone else. There's a little island there, and that's something to look at. So this is phenomenally powerful, this so-called metadata, powerful information. And as far as I know, Leo, this podcast is the first disclosure of what the NSA's PRISM program is, that it is a tap, an optical fiber tap on these companies. I don't know what results from this. But I imagine now Congress will know how to ask some better questions.
Leo: I hope so.
Steve: And these companies will probably want to find out if this is going on.
Leo: Yeah. Steve Gibson is at GRC.com. That's his website, if you want to spy on him. He gives away many, many wonderful security tools including ShieldsUP!. Make sure you check your Plug & Play status there with the ShieldsUP! program. Make sure your router isn't releasing information to the outside world or access to your inside network. You can also get SpinRite. That's his bread and butter, the world's finest hard drive maintenance and recovery utility. And for people with bandwidth issues, the 16Kb version of the show. And if you would like to send a transcript to your elected officials, that might not be a bad idea, and those transcripts are made by Elaine Farris and made available on Steve's site as well, GRC.com.
Steve: Elaine's a little under the weather at the moment.
Leo: I'm sorry, Elaine.
Steve: She didn't know when we were going to get the audio; but, if it came in time, then she thought she'd be able to start on it. So anyway, the point is that we will have full textual transcripts of the podcast in all of its glory a couple days from now, posted on GRC.
Leo: Good, good. You also can go there to ask questions. And we will do a Q&A episode.
Steve: Yup, I imagine we'll have lots of questions. And we'll probably still be talking about this next week.
Leo: Yeah. And that will be GRC.com/feedback, if you'd like to pose a question to Steve Gibson. We've mentioned before he's on Twitter @SGgrc. Follow him there.
Steve: I was just going to say that I just tweeted five bit.ly links to these documents, to some PDF forms and these redacted and redaction-filled-in documents that exist on the 'Net. If anyone's interested in additional information, I mean, it just - it's riveting stuff, really interesting.
Leo: Yeah, it really is. Thank you, Steve Gibson. We do this show every Wednesday. You can find us right here at 11:00 a.m. Pacific, 2:00 p.m. Eastern time, 19:00 UTC on TWiT.tv. Do watch live. Lot of fun. And you're welcome to visit us in-studio, as well. We always have visitors. People love to see you live, Steve. But if you can't, we always have on-demand audio and video after the fact, not only on Steve's site, but high-quality audio MP3s and video, as well, available at TWiT.tv/sn, or wherever you get your podcasts, like iTunes.
Steve: I think I'm going to be up maybe in August.
Leo: Ooh.
Steve: I think Jenny's going to come up to do her regular summer visit of friends, and I thing I'm going to come up, and I'm planning to synchronize it with a Wednesday so I can do the podcast in-studio with you, Leo.
Leo: Great. That would be a lot of fun.
Steve: Yeah, it would be.
Leo: I look forward to that. And I'll buy you...
Steve: Okay, my friend.
Leo: Dinner's on me. Or lunch.
Steve: Okay.
Leo: Thanks, Steve. We'll see you next time...
Steve: Thank you.
Leo: ...on Security Now!.



 \
\