Russian hackers throw Trump victory party new spear phishing
Russian hackers throw Trump victory party with new spear phishing campaign
Russian threat group tied to DNC uses election chaos to hook NGOs, think tanks.
SEAN GALLAGHER - 11/10/2016, 2:40 PM
As Trump was giving his victory speech, a new wave of spear phishing attacks from Russian hackers was already on its way using his win as click-bait.
Gage Skidmore
Less than six hours after Donald Trump won the US presidential election, a new spear phishing campaign was launched by a Russia-based group. The group is apparently one of the two organizations connected to the breach at the Democratic National Committee, and it's responsible for nearly a decade of intelligence collection campaigns against military and diplomatic targets.
Security firm Volexity refers to the group as "the Dukes" based on the malware family being utilized. According to a report by Volexity founder Steven Adair, the group is known for a malware family known as "the Dukes"—also referred to as APT29 or "Cozy Bear." The Dukes' primary targets in this latest round of attacks appear to be non-governmental organizations (NGOs) and policy think tanks in the US.
According to Volexity's data, the threat group sent e-mails from purpose-built Gmail accounts and what may be a compromised e-mail account from Harvard University's Faculty of Arts and Science. The phishing e-mails dropped a new variant of backdoor malware dubbed "PowerDuke" by Volexity, and this malware gave attackers remote access to compromised systems. Volexity has been tracking a number of campaigns based on PowerDuke since August, when some "highly targeted" malicious e-mails were sent to individuals at a number of policy research organizations in the US and Europe. The e-mails were disguised as messages from the Center for a New American Security (CNAS), Transparency International, the Council on Foreign Relations, the International Institute for Strategic Studies (IISS), and Eurasia Group. Another wave of similar e-mails targeted universities in October.
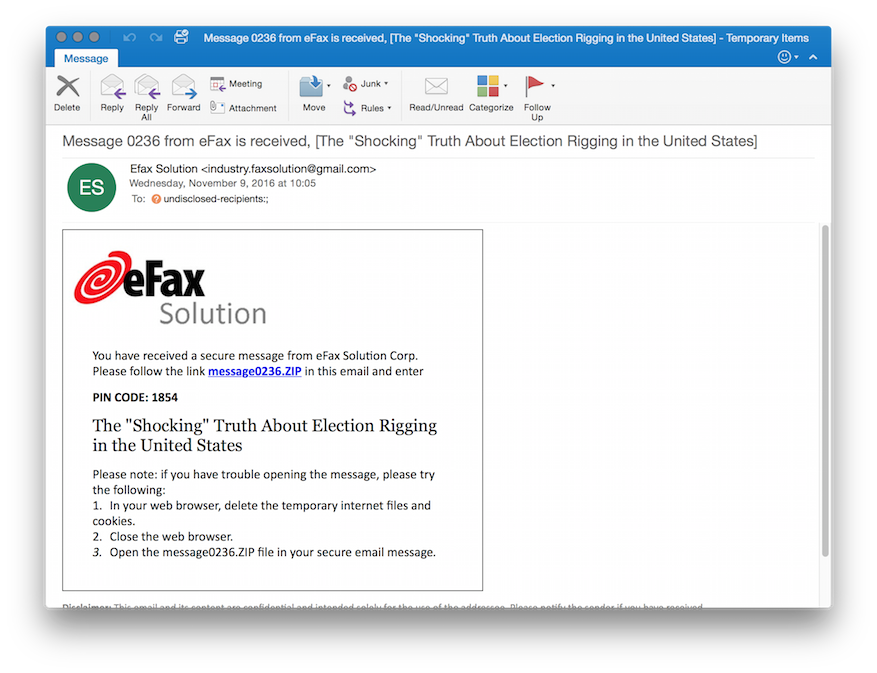
The latest round of e-mails, sent out on November 8 and 9, "were sent in large quantities to different individuals across many organizations and individuals focusing in national security, defense, international affairs, public policy, and European and Asian studies," Adair wrote. "Two of the attacks purported to be messages forwarded on from the Clinton Foundation giving insight and perhaps a postmortem analysis into the elections. Two of the other attacks purported to be eFax links or documents pertaining to the election’s outcome being revised or rigged. The last attack claimed to be a link to a PDF download on 'Why American Elections Are Flawed.'"
A sample of one of the malicious "eFax" messages carrying PowerDuke.
PowerDuke uses steganography to conceal its backdoor's code in a .PNG graphic file. The August attacks used legitimate content from the spoofed senders in Word and Excel documents to fool targets into opening attachments outside of a safe preview mode—scripts then downloaded the .PNG from a compromised Web server. The malware was next extracted from the .PNG and executed by Windows' rundll32.exe, residing only in memory and leaving no trace in the operating system. Once installed, the backdoor contacts a command and control network and allows the attackers to carry out a large range of commands—including the uploading and downloading of files, remote wiping of files, and accessing details about the infected machine, its user, and the network it runs on.
This week's attacks used a combination of approaches to deliver PowerDuke. The e-mails had either malicious links to .ZIP files or forged Windows shortcut files linked to a "clean" Rich Text Format document and a PowerShell script that installed the malware. Two were "eFax" messages; the other three apparently came from the e-mail account of a senior research fellow at Harvard's Center for International Development. Two of those messages were spoofed forwards of messages from the Clinton Foundation using the same Harvard account. In all cases, the malware scripts included a variety of advanced anti-malware detection and virtual machine detection scripts to evade analysis.
"The group’s anti-VM macros and PowerShell scripts appear to have drastically reduced the number of sandboxes and bots that the group has to deal with on their command and control infrastructure," Adair noted. "This combined with their use of stenography to hide their backdoor within PNG files that are downloaded remotely and loaded in memory only or via alternate data streams (ADS) is quite novel in its approach. Volexity believes that the Dukes are likely working to gain long-term access into think tanks and NGOs and will continue to launch new attacks for the foreseeable future."
http://arstechnica.com/security/2016/11 ... -campaign/
Russian hackers accused of post-election attacks on U.S. think tanks
By Jim Finkle and Dustin Volz
A Russian hacking group began attacking U.S.-based policy think tanks within hours of Donald Trump's presidential election victory, according to cyber experts who suspect Moscow is seeking information on the incoming administration.
Three cyber security firms told Reuters that are tracking a spear-phishing campaign by a Russian-government linked group known as Cozy Bear, which is widely suspected of hacking the Democratic Party ahead of the election.
"Probably now they are trying to rush to gain access to certain targets where they can get a better understanding on what is going on in Washington after the election and during the transition period," said Jaime Blasco, chief scientist with cyber security firm AlienVault.
Targets included the Council for Foreign Relations, said Adam Segal, a security expert with the think tank. His colleagues include former U.S. Senator John D. Rockefeller IV and former Reagan administration State Department official Elliott Abrams.
Representatives with the Russian Embassy in Washington could not be reached for comment. Moscow has strongly denied that it was behind the hacks.
Spear-phishing campaigns use malware-tainted emails to infect computers of carefully selected staff at target organizations. They typically appear to be from people whom the victims know and on subjects of interest to them.
Some of the emails appeared to be from Harvard University under the subject line, “Why American Elections are flawed,” according to Washington-based cyber security firm Volexity.
The attacks began as the Obama administration was weighing if and how it might respond in its final two months to a series of high-profile hacks on Democratic Party organizations that U.S. intelligence officials have publicly blamed on Moscow.
A former senior Obama administration official said on Thursday that the White House had decided to take action against Russia after the election but no decision had been made on exactly how to respond.
Options included U.S. prosecutors indicting Russians believed to be behind the attacks, applying new economic sanctions against Moscow and the United States launching a retaliatory cyber attack against Russia, said the former official who asked not to be named.
White House officials feared that retaliating before the election could have led Russia to launch a major cyber attack on the United States that would have disrupted the banking system, power grid or internet service. But they said administration officials had decided that the United States needed to show after the election that it would respond to state-sponsored cyber attacks, said the former official.
Trump has said he is not convinced Russia was behind the attacks. He has yet to fill key national security posts, which makes it difficult to assess how his administration might handle the issue.
Harvard's chief information security officer, Christian Hamer, warned staff about the attacks on Thursday afternoon, saying that federal law enforcement was investigating.
He said some of the emails used in the campaign appeared as if they were sent from members of Harvard's Faculty of Arts and Sciences, using the school's branding.
An FBI representative declined comment.
http://www.reuters.com/article/us-usa-e ... SKBN1352P9
Russian ‘Dukes’ of Hackers Pounce on Trump Win
Less than six hours after Donald Trump became the presumptive president-elect of the United States, a Russian hacker gang perhaps best known for breaking into computer networks at the Democratic National Committee launched a volley of targeted phishing campaigns against American political think-tanks and non-government organizations (NGOs).
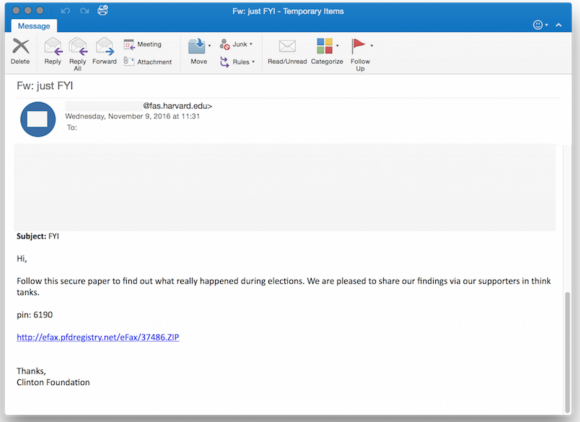
One of the phishing emails in the latest political espionage attack launched by The Dukes. Source: Volexity.
That’s according to a new report from Washington, D.C.-based cyber incident response firm Volexity. The firm’s researchers say they’ve been closely monitoring the activities of an well-established Russian malware development gang known variously as Cozy Bear, APT29, and The Dukes.
Hacking attacks launched by The Dukes were thought to be connected to intrusions at the Democratic National Committee (DNC), as well as cyber break-ins at multiple high-profile United States Government organizations, Volexity reports in a blog post published Thursday morning.
Last month, the Obama administration publicly acknowledged for the first time that it believed that the Russian government was responsible for stealing and disclosing emails from the DNC and a range of other institutions and prominent individuals, most recently Hillary Clinton’s campaign chairman, John D. Podesta. The emails were posted on WikiLeaks and other sites.
Volexity CEO Steven Adair said The Dukes have launched at least five sorties of email-based malware phishing attacks since Trump’s acceptance speech, and that the malware campaigns are ongoing.
“Two of the attacks purported to be messages forwarded on from the Clinton Foundation giving insight and perhaps a postmortem analysis into the elections,” Adair wrote.”Two of the other attacks purported to be eFax links or documents pertaining to the election’s outcome being revised or rigged. The last attack claimed to be a link to a PDF download on “Why American Elections Are Flawed.”
According to Volexity, in July 2015 the Dukes started heavily targeting think tanks and NGOs.
“This represented a fairly significant shift in the group’s previous operations and one that continued in the lead up to and immediately after the 2016 United States Presidential election,” Adair wrote.
Prior to the election, The Dukes were active on August 10, 2016 and on August 25, 2016, launching several waves of highly targeted spear phishing attacks against several U.S.-based think tanks and NGOs.
One of the phishing emails in the latest political espionage attack launched by The Dukes. Source: Volexity.
“These spear phishing messages were spoofed and made to appear to have been sent from real individuals at well-known think tanks in the United States and Europe,” Adair wrote. “These August waves of attacks purported to be from individuals at Transparency International, the Center for a New American Security (CNAS), the International Institute for Strategic Studies (IISS), Eurasia Group, and the Council on Foreign Relations (CFR).”
Adair said the more typical attacks from The Dukes come in the form of slightly less-targeted email blasts — often to just a few dozen recipients at a time — that include booby-trapped Microsoft Office documents.
When launched, the tainted Excel or Word document opens an actual file with real content, but it also prompts the target to enable “macros” — a powerful functionality built into Office documents that hackers can use to automatically download and run malicious code on a Windows system.
The Dukes prefer to launch the attacks using hacked servers and email inboxes belonging to unsuspecting, trusted workers at NGOs and U.S. government systems, Adair explained. Most often, he said, the intruders will repurpose a legitimate document found in one of these hacked inboxes and inject a sophisticated backdoor “trojan horse program.”
If the phishing target opens the document and has macros enabled in Microsoft Office — or allows macros to be run after the decoy document is shown — a malicious script embedded in the macro installs on the target’s system a powerful foothold for the attacker.
Adair said The Dukes have a well-earned reputation for coding and constantly improving their own custom backdoor trojans, but that they’re not known for using so-called “zero day” threats — previously unknown security weaknesses in software and hardware that knowledgeable attackers can use to remotely compromise a target’s computer just by loading a Web page or opening a document.
“In some ways, these guys seem kind of low-budget, but their macros are well-obfuscated and will sail right through just about any [antivirus] tool, appliance or cloud service,” Adair said in an interview.
The Dukes also take great care not to phish security personnel at targeted organizations. For example, if the phishing target has macros enabled in Microsoft Office or allows them to be run after the decoy document is shown, a malicious script embedded in the macro executes a busy little program that scours the target’s computer for signs that it is running on an network administrator’s machine.
If the malicious script detects the user is “admin” or “administrator,” the infection goes no further and the malware shuts down. Likewise, it checks many other signs that it might be running in a “sandbox” environment — a test lab often used by security and malware researchers.
Adair said his although his research team doesn’t have specific insight into to how successful these latest espionage attacks may have been, The Dukes are an effective information- and resource gathering machine.
“My opinion is that if this group got access to a zero-day and it’s something they can embed in a document, they could devastate anyone they target,” Adair said. “This is a well-funded and in some respects professional organization. What they’re doing takes time and effort, and for eight plus years now they’ve been in continuous development of new backdoors. They’re continually targeting different verticals — universities, NGOs and governments — and they learn from others, retool and modify their attacks constantly.”
As The New York Times reported last month, “President Obama is weighing a ‘proportional’ response to Russia’s efforts to interfere with this fall’s election campaign through hacking.
Thursday morning, security vendor Kaspersky Lab warned that a massive cyberattack hit five of Russia’s largest banks. Kaspersky said in a statement that the distributed denial of service attacks (DDoS) began Tuesday at 1830 IST and targeted “the websites of at least five well-known financial institutions in the top 10” in Russia.
It remains unclear who launched the bank cyberattacks, which are reportedly ongoing. Kaspersky said the attack on Russia’s banking system is apparently being launched by a network of more than 24,000 hacked Internet of Things (IoT) devices, and that more than half of the hacked things were in the United States, India, Taiwan and Israel.
Further reading on the storied hacking history of The Dukes:
F-Secure calls them CozyDuke (PDF). FireEye‘s take (PDF). Crowdstrike on Cozy Bear.
https://krebsonsecurity.com/2016/11/rus ... trump-win/