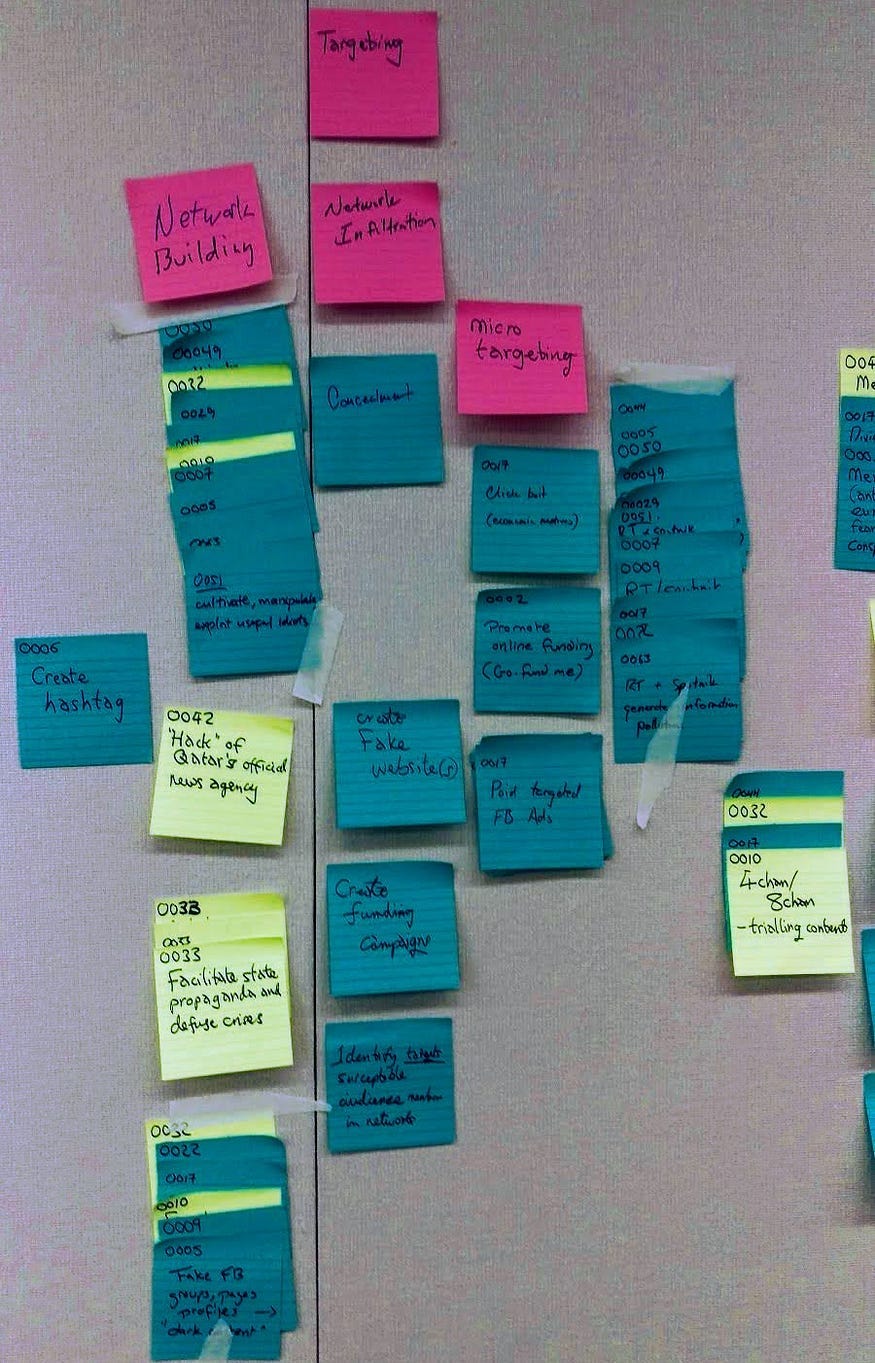
Belligerent Savant » Thu Nov 16, 2023 9:39 pm wrote:.
My primary concerns, as is often the case, are with the underlying drivers behind any substantive proposed policy changes/shifts rather than the front-facing talking points/attempted justifications.
I have minimal faith in either political party placing the interests of The People as a priority over other interests.
Indeed, more often than not underlying issues (that later inspire the clamoring for ‘change’) are at times intentional, part of larger/longer-term objectives that are generally (or exclusively) detrimental to the collective.
Variations of the Bait and Switch and/or Trojan Horse.
This is the worst kind of conspiracy thinking. It's all part of the plan, and anything that contradicts it is just a deeper level of the plan. It's impossible to argue with because anything can be twisted around to be part of the plan.
Anyway, a more nuanced take than the republican/telecom propaganda you and Grizzly posted:
https://arstechnica.com/tech-policy/202 ... nd-prices/
Internet providers say the FCC should not investigate broadband prices
ISPs say anti-discrimination rule should cover only deployment, not prices.
Jon Brodkin - 11/8/2023, 9:57 PM
Internet service providers and their lobby groups are fighting a US plan to prohibit discrimination in access to broadband services. In particular, ISPs want the Federal Communications Commission to drop the plan's proposal to require that prices charged to consumers be non-discriminatory.
In 2021, Congress required the Federal Communications Commission to issue rules "preventing digital discrimination of access based on income level, race, ethnicity, color, religion, or national origin" within two years. FCC Chairwoman Jessica Rosenworcel last month released her draft plan to comply with the congressional mandate and scheduled a November 15 commission vote on adopting final rules.
The plan is likely to pass in a party-line vote as Rosenworcel has a 3-2 Democratic majority, but aspects of the draft could be changed before the vote. Next week's meeting could be a contentious one, judging by a statement issued Monday by Republican Commissioner Brendan Carr.
Carr described Rosenworcel's proposal as "President Biden's plan to give the administrative state effective control of all Internet services and infrastructure in the US." He also objects to the Rosenworcel plan's statement that the FCC rules may apply to entities that are not broadband providers, such as landlords, if they "impede equal access to broadband Internet access service."
Consumer advocates generally support the proposal but say the planned system for handling complaints, ISP responses, and investigations is not transparent enough, reducing the system's potential to act as a deterrent. Consumer advocates also say Internet users who have already been harmed by discrimination may not get any relief because the proposed rules do not apply retroactively.
ISPs: Don’t investigate our prices
ISPs including Comcast, Charter, AT&T, and Verizon have held a flurry of meetings with FCC officials and commissioners in which they argued that the rules are too broad. The broadband firms are especially concerned about the FCC's plan to consider the prices consumers pay when determining whether an ISP practice is discriminatory. The industry wants the FCC to consider only the deployment of broadband, not other factors such as how much it costs.
In a meeting with Rosenworcel's staff, cable company executives "stated that the Draft Order would impose overbroad liability standards that impede further broadband investment and are legally vulnerable by adopting a disparate impact rather than a disparate treatment liability approach," according to an ex parte filing submitted yesterday by cable lobby group NCTA-The Internet & Television Association. The meeting included executives from Comcast, Charter, and Cox.
The cable companies said the FCC "should define digital discrimination as disparate treatment and should limit the standard to policies and practices involving the deployment of broadband network facilities. It should not regulate rates or non-technical aspects of broadband service." The cable industry filing said "it is especially important for the Commission to exclude 'price' from the list of 'covered elements of service.'"
Similar arguments were raised by wireless industry trade group CTIA. "Evaluating matters such as pricing, deposits, discounts, and data caps is price regulation because the Commission may levy consequences based on the price per level of service that a provider chooses to offer," CTIA said. "Commission evaluation of price is unnecessary in the competitive wireless marketplace and may deter offering discounts and enticements to switch providers that consumers enjoy today."
More opposition came in filings submitted by AT&T, Verizon, and the USTelecom industry group. ISPs and their trade groups will likely sue the FCC if the rules are approved.
"The draft rules ignore the statute's clear focus on broadband deployment and instead cast a net so wide it would capture every business decision a provider makes concerning how to sell its product, with little regard to the reasonableness (or usefulness) of that decision," AT&T said. "This regulatory overreach will impose unnecessary regulation on broadband providers and divert attention and vital resources from broadband investment and deployment at this key juncture in the bipartisan Infrastructure Act's Broadband, Equity, Access & Deployment Program (BEAD)." That's a reference to a $42 billion grant program that will pay ISPs to expand their networks.
ISPs previously complained about an unrelated rule requiring them to list all their monthly fees, but the FCC rejected their complaints and issued the rule.
Defining discrimination
Rosenworcel's plan defines digital discrimination of access as "policies or practices, not justified by genuine issues of technical or economic feasibility, that differentially impact consumers' access to broadband Internet access service based on their income level, race, ethnicity, color, religion, or national origin or are intended to have such differential impact."
The draft order says the new rules "do not set rates for broadband Internet access service and are not an attempt to institute rate regulation." Instead, the commission would investigate potential discrimination on a case-by-case basis.
Discrimination would not have to be intentional in order for the FCC to rule against an ISP. A fact sheet from Rosenworcel's office says the FCC would "investigate possible instances of discrimination of broadband access, work to solve and—when necessary—penalize companies for failing to meet the obligations defined in the rules." That applies to "policies and practices if they differentially impact consumers' access to broadband Internet access service or are intended to do so."
As noted earlier, the rules would not apply retroactively. The draft order concludes that the FCC does not have authority "to require covered entities to undertake remedial measures to eradicate the effects of conduct predating the effective date of our rules."
The proposed rules "apply to any lack of comparability in service quality." The plan says the "covered elements of service" that could be evaluated in FCC investigations include but are not limited to the following:1. Deployment of broadband infrastructure, network upgrades, and network maintenance;
2. Service quality components and the terms and conditions on which broadband Internet access service is provided, including but not limited to speeds, capacities, latency, data caps, throttling, pricing, promotional rates, imposition of late fees, opportunity for equipment rental, installation time, contract renewal terms, service termination terms, and use of customer credit and account history;
3. Marketing, advertisement, and outreach; and
4. Technical service, onsite service, and other provision of customer service.
The draft order rejected a suggestion to allow disparities in broadband deployment and terms if those disparities can be "explained by differences in the profitability of serving the different areas." That approach "would limit the Commission to considering 'profitability' rather than 'issues of technical and economic feasibility,' and would appear to place primary weight on economic rather than technical considerations. Our adopted rule properly includes both technical and economic considerations," the draft says.
Chair defends pricing rule
Despite the FCC statement that it isn't regulating rates, cable companies argue that "the language of the Draft Order would, in fact, regulate rates."
"Regulation of price or non-technical elements, such as marketing, advertising, discounts, or credit checks, would represent a regulatory sea change for the Commission that is inconsistent with the statute," the cable companies' filing said. "Further, this exceptionally broad scope would make provider compliance with and Commission administration of the Draft Order nearly impossible."
Rosenworcel already rejected similar industry arguments that were raised by ISPs during a public comment period. "We reject arguments that we should limit the scope of covered elements of service to deployment practices or technical terms of service, or that we exclude certain terms, such as pricing," the chairwoman's proposal said.
The draft order said the law's "inclusion of 'other quality of service metrics' and 'comparable terms and conditions' in the definition of 'equal access' reflects Congressional intent and authorization that the Commission's digital discrimination of access rules cover any aspect of broadband Internet access service that impedes, impairs or denies 'equal access' to that service." The order goes on to say that "pricing is often the most important term that consumers consider when purchasing goods and services," and this "is no less true with respect to broadband Internet access service."
"Consequently, we do not believe it was necessary for Congress to specifically reference pricing in the definition of 'equal access' because the most natural reading of 'terms and conditions' includes pricing," the draft order said. "The Commission need not prescribe prices for broadband Internet access service, as some commenters have cautioned against, in order to determine whether prices are 'comparable' within the meaning of the equal access definition. The record reflects support for the Commission ensuring pricing consistency as between different groups of consumers."
The draft also points out that US law requires the FCC to prevent both "digital discrimination of access" and "deployment discrimination."
"Had Congress wished to limit the scope of section 60506(b) to 'deployment discrimination,' it would have done so explicitly," the draft plan says. "The use of two different terms ('digital discrimination of access' and 'deployment discrimination') in adjacent subsections of a one-page section of the statute clearly indicates that Congress intended the two terms to have different meanings."
Verizon's filing argued that "when Congress intends to grant authority over 'pricing' or 'rates'—as well as other terms and conditions—it includes those words explicitly. It did not do so in Section 60506."
"The importance of pricing to a customer's purchasing decision and Congress's decision to omit 'rates' or 'pricing' and use only 'terms and conditions' demonstrates that Congress did not want the Commission's digital discrimination inquiry to include prices," Verizon said.
Republican blasts “government control”
Carr objected to the long list of "covered elements of service," saying it "empowers the FCC to regulate every aspect of the Internet sector for the first time ever," and "is motivated by an ideology of government control that is not compatible with the fundamental precepts of free market capitalism."
Carr raised concerns about the plan applying to more than just ISPs. Rosenworcel's draft plan says the FCC "disagree[s] with arguments that our authority under 60506(b) extends only to providers of broadband Internet access service." For example, the draft order does not exempt local governments from the rules "based on their roles as right-of-way managers or franchise regulators," because "any entity that meaningfully affects access to broadband Internet service is subject to our digital discrimination of access rules."
Rosenworcel's plan mentions the scenario of a "landlord restricting broadband options within a building even if multiple providers are available," but is vague on exactly what kinds of companies that aren't ISPs would have to comply with the rules.
"While we reach no conclusion whether this, or other specific examples in the record would be covered by our rules, we are persuaded that there could be situations—now or in the future—in which non-providers could impede equal access to broadband Internet access service based on the listed characteristics," Rosenworcel's draft plan said.
According to Carr, "Landlords are now covered, construction crews are now covered, marketing agencies are now covered, banks are now covered, the government itself is now covered—all newly regulated by the FCC and liable for any act or omission that the agency determines has an impermissible impact on a consumer's access to broadband. Congress never authorized the FCC to regulate these industries or entities."
Carr also pointed to a portion of the FCC draft order that says, "in order to fully effectuate the goals of section 60506, we find that our rules must cover both actions and omissions, whether recurring or a single instance, concerning these aspects of service, that defeat comparability of service quality, terms, and conditions."
Carr's interpretation is that, "if you take any action, you may be liable, and if you do nothing, you may be liable. There is no path to complying with this standardless regime. It reads like a planning document drawn up in the faculty lounge of a university's Soviet Studies Department."
Consumer advocates’ complaints
Consumer advocacy groups mostly supported the rules but offered some criticisms. The National Digital Inclusion Alliance (NDIA) asked how the FCC "will address present conditions, given that the draft Order declined to impose 'retroactive liability' and will focus instead on preventing and eliminating digital discrimination of access that occurs after the effective date of the rules."
The NDIA urged the commission "to provide guidance articulating what evidence it will consider to evaluate ongoing behavior, such as the persistent gaps in AT&T's broadband technology and speeds offered to locations in higher and lower-income Census tracts in Cleveland."
Consumer advocacy group Public Knowledge said the draft plan "is strong, and if rigorously enforced will prevent future inequality of access." But the proposed complaint process isn't transparent enough, the group said.
"First, the Commission does not propose to share any response by the ISP with the complainant," Public Knowledge wrote. "Indeed, the Commission does not propose to inform the complainant of the outcome of their complaint, what steps the Commission has taken, or in any way to communicate with the complainant after the filing of the complaint... Failure to communicate with the complainant on these matters will create a feeling of futility on the part of complainants and organizations representing complainants that will discourage the filing of meritorious complaints."
A requirement to send updates to complainants would "provide a necessary check on the Commission's discretion," Public Knowledge said. "Because the Commission has created a system that lies entirely within the Commission's discretion—including when and how the Commission will release aggregate or de-anonymized data—it will be impossible to verify whether and to what extent the Commission takes its responsibilities under [the 2021 discrimination law] seriously."
The FCC has what it calls informal and formal complaint processes, and it intends to use its informal process to handle discrimination complaints. Public Knowledge argues that the formal complaint process would be better because the "risk of public shaming supported by discovery by complainants and the ultimate adjudication of the Commission will cause ISPs guilty of digital discrimination to restrain their actions—or seek settlement quickly to avoid further embarrassment."
The group also urged the commission to "adopt rules that protect complainants from retaliation." Because complaints will be shared with ISPs, broadband providers "may retaliate against complainants to discourage future complaints," the group said.
The National Coalition on Black Civic Participation urged the FCC to establish a civil rights office and publish an annual State of Digital Discrimination Report that includes the FCC's "findings of digital discrimination, the steps the Commission has taken to facilitate equitable access to broadband in protected communities, and the final resolution of digital discrimination complaints."