They Know Much More Than You ThinkIn mid-May, Edward Snowden, an American in his late twenties, walked through the onyx entrance of the Mira Hotel on Nathan Road in Hong Kong and checked in. He was pulling a small black travel bag and had a number of laptop cases draped over his shoulders. Inside those cases were four computers packed with some of his country’s most closely held secrets.
Within days of Snowden’s documents appearing in The Guardian and The Washington Post, revealing several of the National Security Agency’s extensive domestic surveillance programs, bookstores reported a sudden spike in the sales of George Orwell’s classic dystopian novel 1984. On Amazon.com, the book made the “Movers & Shakers” list and skyrocketed 6,021 percent in a single day. Written sixty-five years ago, it described a fictitious totalitarian society where a shadowy leader known as “Big Brother” controls his population through invasive surveillance. “The telescreens,” Orwell wrote, “have hidden microphones and cameras. These devices, alongside informers, permit the Thought Police to spy upon everyone….”
Today, as the Snowden documents make clear, it is the NSA that keeps track of phone calls, monitors communications, and analyzes people’s thoughts through data mining of Google searches and other online activity. “Any sound that Winston made, above the level of a very low whisper, would be picked up by it,” Orwell wrote about his protagonist, Winston Smith.
There was of course no way of knowing whether you were being watched at any given moment. How often, or on what system, the Thought Police plugged in on any individual wire was guesswork. It was even conceivable that they watched everybody all the time. But at any rate they could plug in your wire whenever they wanted to. You had to live—did live, from habit that became instinct—in the assumption that every sound you made was overheard, and, except in darkness, every movement scrutinized.
Of course the US is not a totalitarian society, and no equivalent of Big Brother runs it, as the widespread reporting of Snowden’s information shows. We know little about what uses the NSA makes of most information available to it—it claims to have exposed a number of terrorist plots—and it has yet to be shown what effects its activities may have on the lives of most American citizens. Congressional committees and a special federal court are charged with overseeing its work, although they are committed to secrecy, and the court can hear appeals only from the government.
Still, the US intelligence agencies also seem to have adopted Orwell’s idea of doublethink—“to be conscious of complete truthfulness,” he wrote, “while telling carefully constructed lies.” For example, James Clapper, the director of national intelligence, was asked at a Senate hearing in March whether “the NSA collect[s] any type of data at all on millions or hundreds of millions of Americans.” Clapper’s answer: “No, sir…. Not wittingly.”
Three months later, following the revelations of the phone-log program in which the NSA collects telephone data—the numbers of both callers and the length of the calls—on hundreds of millions of Americans, Clapper switched to doublethink. He said that his previous answer was not a lie; he just chose to respond in the “least untruthful manner.” With such an Orwellian concept of the truth now being used, it is useful to take a look at what the government has been telling the public about its surveillance activities over the years, and compare it with what we know now as a result of the top secret documents and other information released by, among others, the former NSA contract employee Edward Snowden.
Looking back, the NSA and its predecessors have been gaining secret, illegal access to the communications of Americans for nearly a century. On July 1, 1920, a slim balding man in his early thirties moved into a four-story townhouse at 141 East 37th Street in Manhattan. This was the birth of the Black Chamber, the NSA’s earliest predecessor, and it would be hidden in the nondescript brownstone. But its chief, Herbert O. Yardley, had a problem. To gather intelligence for Woodrow Wilson’s government, he needed access to the telegrams entering, leaving, and passing through the country, but because of an early version of the Radio Communications Act, such access was illegal. With the shake of a hand, however, Yardley convinced Newcomb Carlton, the president of Western Union, to grant the Black Chamber secret access on a daily basis to the private messages passing over his wires—the Internet of the day.
For much of the next century, the solution would be the same: the NSA and its predecessors would enter into secret illegal agreements with the telecom companies to gain access to communications. Eventually codenamed Project Shamrock, the program finally came to a crashing halt in 1975 when a Senate committee that was investigating intelligence agency abuses discovered it. Senator Frank Church, the committee chairman, labeled the NSA program “probably the largest governmental interception program affecting Americans ever undertaken.”
As a result of the decades of illegal surveillance by the NSA, in 1978 the Foreign Intelligence Surveillance Act (FISA) was signed into law and the Foreign Intelligence Surveillance Court (FISC) came into existence. Its purpose was, for the first time, to require the NSA to get judicial approval for eavesdropping on Americans. Although the court seldom turned down a request for a warrant, or an order as it’s called, it nevertheless served as a reasonable safeguard, protecting the American public from an agency with a troubling past and a tendency to push the bounds of spying unless checked.
For a quarter of a century, the rules were followed and the NSA stayed out of trouble, but following the September 11 attacks, the Bush administration decided to illegally bypass the court and began its program of warrantless wiretapping. “Basically all rules were thrown out the window and they would use any excuse to justify a waiver to spy on Americans,” I was told by Adrienne J. Kinne, who in 2001 was a twenty-four-year-old voice intercept operator who conducted some of the eavesdropping. She or her superiors did not have to get a warrant for each interception. “It was incredibly uncomfortable to be listening to private personal conversations of Americans,” she said. “And it’s almost like going through and stumbling and finding somebody’s diary and reading it.”
All during this time, however, the Bush administration was telling the American public the opposite: that a warrant was obtained whenever an American was targeted. “Anytime you hear the United States government talking about a wiretap, it requires—a wiretap requires a court order,” President George W. Bush told a crowd in 2004. “Nothing has changed, by the way. When we’re talking about chasing down terrorists, we’re talking about getting a court order before we do so.” After exposure of the operation by The New York Times in 2005, however, rather than strengthen the controls governing the NSA’s spying, Congress instead voted to weaken them, largely by codifying into the amendment to FISA what had previously been illegal.
At the same time, rather than calling for prosecution of the telecom officials for their role in illegally cooperating in the eavesdropping program, or at least a clear public accounting, Congress simply granted them immunity not only from prosecution but also from civil suits. Thus, for nearly a century, telecom companies have been allowed to violate the privacy of millions of Americans with impunity.
With the arrival of the Obama administration, the NSA’s powers continued to expand at the same time that administration officials and the NSA continued to deceive the American public on the extent of the spying. In addition to the denial I have mentioned by James Clapper, General Keith Alexander, the NSA director, also blatantly denied that his agency was keeping records on millions of Americans. In March 2012, Wired magazine published a cover story I wrote on the new one-million-square-foot NSA data center being built in Bluffdale, Utah. In the article, I interviewed William Binney, a former high-ranking NSA official who was largely responsible for automating the agency’s worldwide eavesdropping network. He quit the agency in 2001 in protest after he saw the system designed mainly for intelligence about foreign threats turned inward on the American public. In the interview, he told how the agency was tapping into the country’s communications and Internet networks. He revealed that it also was secretly obtaining warrantless access to billions of phone records of Americans, including those of both AT&T and Verizon. “They’re storing everything they gather,” he said.
In the months afterward, General Alexander repeatedly denied Binney’s charges. “No…we don’t hold data on US citizens,” he told Fox News, and at an Aspen Institute conference he said, “To think we’re collecting on every US person…that would be against the law.” He added, “The fact is we’re a foreign intelligence agency.”
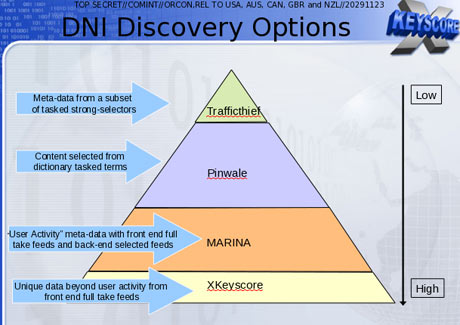
But the documents released by Edward Snowden show that the NSA does have a large-scale program to gather the telephone records of every Verizon customer, including local calls, and presumably a similar agreement with AT&T and other companies. These are records of who called whom and when, not of the content of the conversations, although the NSA has, by other methods, access to the content of conversations as well. But the NSA has, on a daily basis, access to virtually everyone’s phone records, whether cell or landline, and can store, data-mine, and keep them indefinitely. Snowden’s documents describing the PRISM program show that the agency is also accessing the Internet data of the nine major Internet companies in the US, including Google and Yahoo.
Snowden’s documents and statements add greatly to an understanding of just how the NSA goes about conducting its eavesdropping and data-mining programs, and just how deceptive the NSA and the Obama administration have been in describing the agency’s activities to the American public. In a video interview conducted in his room in the Mira Hotel, Snowden elaborated on the extent of the NSA’s capabilities. “Any analyst at any time can target anyone, any selector, anywhere,” he said.
Where those communications will be picked up depends on the range of the sensor networks and the authorities that that analyst is empowered with. Not all analysts have the ability to target everything. But I sitting at my desk certainly had the authorities to wiretap anyone, from you or your accountant to a federal judge to even the president, if I had a personal e-mail [address].
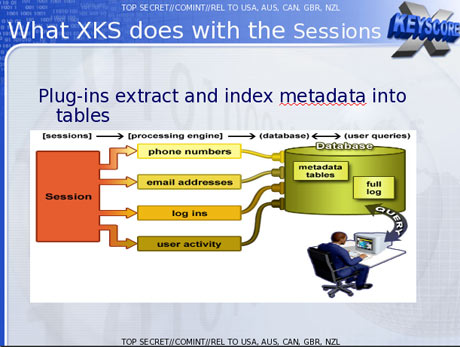
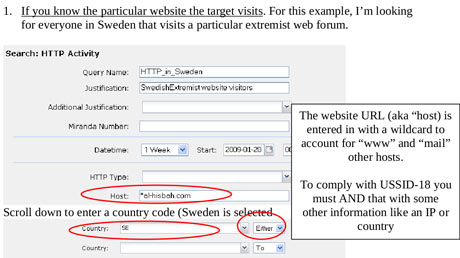
What Snowden was discussing was the way in which analysts at the NSA can place such things as names, phone numbers, and e-mail addresses on target lists, thus causing communications containing those “selectors” to be intercepted. He seemed to be indicating—although this remains to be officially confirmed—that while under FISA, a court order would be required to enter an American on a target list, analysts have the capability to unilaterally bypass the procedure by simply listing a name or e-mail address on the target list. To understand what Snowden is saying, it is necessary to elaborate a bit on the way the NSA conducts its eavesdropping.
DDuring the past decade, the NSA has secretly worked to gain access to virtually all communications entering, leaving, or going through the country. A key reason, according to the draft of a top secret NSA inspector general’s report leaked by Snowden, is that approximately one third of all international telephone calls in the world enter, leave, or transit the United States. “Most international telephone calls are routed through a small number of switches or ‘chokepoints’ in the international telephone switching system en route to their final destination,” says the report. “The United States is a major crossroads for international switched telephone traffic.” At the same time, according to the 2009 report, virtually all Internet communications in the world pass through the US. For example, the report notes that during 2002, less than one percent of worldwide Internet bandwidth—i.e., the international link between the Internet and computers—“was between two regions that did not include the United States.”
Accessing this data is possible through a combination of techniques. Through the most effective of them, the NSA can gain direct access to the fiber-optic cables that now carry most kinds of communications data. According to a slide released by Snowden, the cable-tapping operation is codenamed “UPSTREAM” and it is described as the “collection of communications on fiber cables and infrastructure as data flows past.” It also appears to be both far more secret and far more invasive than the PRISM program revealed by Snowden. Although PRISM gives the NSA access to data from the individual Internet companies, such as Yahoo, Google, and Microsoft, the companies claim that they don’t give the agency direct access to their servers. Through UPSTREAM, however, the agency does get direct access to fiber-optic cables and the supporting infrastructure that carries nearly all the Internet and telephone traffic in the country.
As part of its cable-tapping program, the NSA has secretly installed what amount to computerized filters on the telecommunications infrastructure throughout the country. According to the leaked inspector general’s report, the agency has secret cooperative agreements with the top three telephone companies in the country. Although the report disguises their names, they are likely AT&T, Verizon, and Sprint:
NSA determined that under the Authorization it could gain access to approximately 81% of the international calls into and out of the United States through three corporate partners: Company A had access to 39%, Company B 28%, and Company C 14%.
The filters are placed at key junction points known as switches. For example, much of the communications—telephone and Internet—to and from the northwestern United States pass through a nearly windowless nine-story building at 611 Folsom Street in San Francisco. This is AT&T’s regional switching center. In 2003, the NSA built a secret room in the facility and filled it with computers and software from a company called Narus. Established in Israel by Israelis, and now owned by Boeing, Narus specializes in spyware, equipment that examines both the metadata—the names and addresses of people communicating on the Internet—and the content of digital traffic such as e-mail as it zooms past at the speed of light.
The agency also has access to the telephone metadata—the numbers called and calling and other details—of all Americans. Phone calls from telephone numbers that have been selected as targets can be routed directly to the agency and recorded. According to William Binney, the former NSA senior official, the NSA has established between ten and twenty of these secret rooms at telecom company switches around the country.
It is this daily access to the telephone metadata of all Americans without FISA warrants that the NSA and the Office of National Intelligence tried to hide when they falsely denied that the agency had surveillance records on millions of Americans. For years, the agency also had a nationwide bulk e-mail and Internet metadata collection and storage program, although that was ended in 2011 for “operational and resource reasons,” according to the director of national intelligence.
But according to a joint statement issued on July 2 by senators Ron Wyden and Mark Udall, the real reason the program was shut down was that the NSA was “unable” to prove the usefulness of the operation. “We were very concerned about this program’s impact on Americans’ civil liberties and privacy rights,” they said, “and we spent a significant portion of 2011 pressing intelligence officials to provide evidence of its effectiveness. They were unable to do so, and the program was shut down that year.” The senators added, “It is also important to note that intelligence agencies made statements to both Congress and the [FISA court] that significantly exaggerated this program’s effectiveness. This experience demonstrates to us that intelligence agencies’ assessment of the usefulness of particular collection program—even significant ones—are not always accurate.”
Speaking on Meet the Press, Glenn Greenwald, a lawyer and journalist who wrote the story about the NSA’s collection of phone data for The Guardian, also mentioned a still-secret eighty-page FISA court opinion that, he said, criticized the NSA for violation of both the Fourth Amendment and the FISA statute. According to Greenwald, “it specifically said that they are collecting bulk transmissions, multiple conversations from millions of Americans…and that this is illegal.” The NSA, he said, “planned to try to accommodate that ruling.” On the same program, Representative Mike Rogers, Republican chairman of the House Intelligence Committee, confirmed that the FISA court had issued a critical opinion and said that the NSA had “figured out how to correct that.”
According to The Economist of June 29, “the NSA provided congressional intelligence committees with what it said were over 50 cases in which the programmes disclosed by Mr. Snowden had contributed to the ‘understanding and, in many cases, disruption’ of terrorist plots in America, and over 20 other countries.” In a recent New York Review blog post, Kenneth Roth, director of Human Rights Watch and a former federal prosecutor, commented that “upon scrutiny” many of the plots referred to by the NSA
appear in fact to have been uncovered not because of the mass collection of our metadata but through more traditional surveillance of particular phone numbers or e-mail addresses—the kinds of targeted inquiries that easily would have justified a judicial order allowing review of records kept by communications companies or even monitoring the content of those communications.
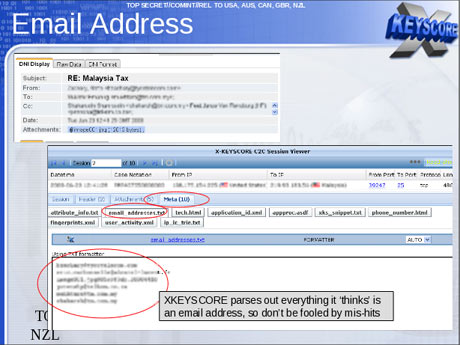
At the AT&T facility on Folsom Street and the other locations, fiber-optic cables containing millions of communications enter the building and go into what’s known as a beam-splitter. This is a prism-type device that produces a duplicate, mirror image of the original communications. The original beams, containing Internet data, continue on to wherever they were originally destined. The duplicate beam goes into Room 641A, the NSA’s secret room one floor below, a discovery made by another whistleblower, AT&T technician Mark Klein. There the Narus equipment scans all the Internet traffic for “selectors”—names, e-mail address, words, phrases, or other indicators that the NSA wants to know about. Any message containing a selector is then retransmitted in full to the NSA for further analysis, as are the contents of phone calls selected. With regard to targeted phone numbers, the agency supplies them to the company, which then gives the NSA access to monitor them.
The selectors are inserted by remote control into the Narus equipment by NSA analysts sitting at their desks at the agency’s headquarters at Fort Meade in Maryland or at dozens of locations around the world. What Snowden seemed to be saying in his interview is that as long as certain analysts have an e-mail address, for example, they can simply enter that information into the system and retrieve the content of the e-mails sent from and to that address. There are, by his account, no judicial checks and balances to assure that the targeting of an American has been approved by a FISA court order and not just by NSA employees. These claims by Snowden, and other revelations from the documents he released, should be investigated by either a select committee of Congress, such as the Church Committee, or an independent body, like the 9/11 Commission.
While UPSTREAM captures most of the telecommunications—about 80 percent according to Binney—there are still gaps in the coverage. That is where the PRISM program comes in. With PRISM, the NSA is able to go directly to the communications industry, including the major Internet companies, to get whatever they miss from UPSTREAM. According to the top secret inspector general’s report, the “NSA maintains relationships with over 100 US companies,” adding that the US has the “home field advantage as the primary hub for worldwide telecommunications.”
According to a recent slide released by Snowden, the NSA on April 5, 2013, had 117,675 active surveillance targets in the program and was able to access real-time data on live voice, text, e-mail, or Internet chat services, in addition to analyzing stored data.
In the end, both UPSTREAM and PRISM may be only the tips of a much larger system. Another new document released by Snowden says that on New Year’s Eve, 2012, SHELLTRUMPET, a metadata program targeting international communications, had just “processed its One Trillionth metadata record.” Started five years ago, it noted that half of that trillion was added in 2012. It also noted that two more new programs, MOONLIGHTPATH and SPINNERET, “are planned to be added by September 2013.”
One man who was prescient enough to see what was coming was Senator Frank Church, the first outsider to peer into the dark recesses of the NSA. In 1975, when the NSA posed merely a fraction of the threat to privacy it poses today with UPSTREAM, PRISM, and thousands of other collection and data-mining programs, Church issued a stark warning:
That capability at any time could be turned around on the American people and no American would have any privacy left, such [is] the capability to monitor everything: telephone conversations, telegrams, it doesn’t matter. There would be no place to hide. If this government ever became a tyranny, if a dictator ever took charge in this country, the technological capacity that the intelligence community has given the government could enable it to impose total tyranny, and there would be no way to fight back, because the most careful effort to combine together in resistance to the government, no matter how privately it was done, is within the reach of the government to know. Such is the capability of this technology…. I don’t want to see this country ever go across the bridge. I know the capacity that is there to make tyranny total in America, and we must see to it that this agency and all agencies that possess this technology operate within the law and under proper supervision, so that we never cross over that abyss. That is the abyss from which there is no return.
Church sounds as if he had absorbed the lessons of 1984. From the recent evidence, they are still to be learned.
—July 12, 2013