
Moderators: Elvis, DrVolin, Jeff
I’m still baffled as to why so many Americans and RI posters have such a hard time believing that Russia could be actively cyber attacking the US and that the Skripal poisoning and anything and everything Russia is accused of doing is baseless propaganda against “the bear.”
UK scientists unable to prove Russia made nerve agent
2018-04-03
The head of the British military facility analysing the Novichok nerve agent used to poison former Russian spy Sergei Skripal and his daughter said Tuesday it has "not identified the precise source" of the substance.
Gary Aitkenhead, chief executive of the Porton Down defence laboratory, told Britain's Sky News that analysts had identified it as military-grade Novichok, but they had not proved it was made in Russia.
"We have not identified the precise source, but we have provided the scientific info to government who have then used a number of other sources to piece together the conclusions," he said.
"It is our job to provide the scientific evidence of what this particular nerve agent is. We identified that it is from this particular family and that it is a military grade, but it is not our job to say where it was manufactured."
Aitkenhead added that "extremely sophisticated methods" were needed to create the nerve agent, and that was "something only in the capabilities of a state actor".
Sergei Skripal and his daughter have been in hospital since March 4 after the poisoning in Britain that London and its major Western allies have blamed on Russia.
The first use of chemical weapons in Europe since World War II has chilled Moscow's relations with the West, as both sides have expelled scores of diplomats.
Moscow has denied any involvement in the incident, with Russian Foreign Minister Sergei Lavrov on Monday suggesting that the British government may be behind the poisoning to distract attention from problems around Brexit.
Aitkenhead would not comment on whether Porton Down had developed or keeps stocks of Novichok, but he dismissed claims the agent used to poison the Skripals had come from the site.
"There is no way anything like that could have come from us or left the four walls of our facility," he said.
The Organisation for the Prohibition of Chemical Weapons (OPCW), the world's chemical watchdog, will meet Wednesday to discuss Britain's allegations that Russia was responsible for the poisoning, according to documents released on Tuesday.
It said Russia asked the OPCW, which has received samples of the Novichok used that it has been analysing, for the meeting.
The confidential gathering will start at 10:00 am (0800 GMT) at its headquarters in The Hague.
(AFP)
http://www.france24.com/en/20180403-uk-skripal-salisbury-russia-nerve-agent-novichok-porton-down
Heaven Swan » Tue Apr 03, 2018 11:04 am wrote:I’m still baffled as to why so many Americans and RI posters have such a hard time believing that Russia could be actively cyber attacking the US and that the Skripal poisoning...
British scientists at the Porton Down defence research laboratory have not established that the nerve agent used to poison Sergei and Yulia Skripal was made in Russia, it has emerged.
You argue that the source of this nerve agent, Novichok, is Russia. How did you manage to find it out so quickly? Does Britain possess samples of it?
Let me be clear with you … When I look at the evidence, I mean the people from Porton Down, the laboratory …
So they have the samples …
They do. And they were absolutely categorical and I asked the guy myself, I said, "Are you sure?" And he said there's no doubt.
Anyway, I hope that goes a little way towards helping you understand where I - and quite a few Brits - are coming from.
Belligerent Savant » Sun Mar 25, 2018 6:59 pm wrote:.
A markedly distinct analysis compared to the white noise offered by MSM:Belligerent Savant » Sun Mar 25, 2018 11:33 am wrote:.
https://medium.com/homefront-rising/dum ... fa522ff44f
Excerpt:
“If I give you a malware binary to reverse engineer, what do you see?” This is the question that had been posited by Michael Tanji, the retired cyber intelligence analyst. “Exactly what the author wants you to see.”
I want you to see words in a language that would throw suspicion on someone else.
An article published in ArsTechnica highlighted the work of an independent security researcher, Adam Carter, who had uncovered evidence that some of the documents released by Guccifer 2.0 in his initial document dump had been manipulated in a manner which introduced Russian words, in the Cyrillic alphabet, into the metadata of the documents, including a reference to “Felix Edmundovich,” the first name and patronymic of the founder of the Soviet security service, Felix Dzerzhinsky. The combination of the Cyrillic alphabet and the reference to a Russian spymaster seems ideal if one is trying to attribute its existence to the Russian intelligence services.
I want you to see that my code was compiled in a particular foreign language (even though I only read and/or write in a totally different language).
FireEye, a well-known cyber security company, has written a report on APT-28 (another name for Fancy Bear), highlights a number of Russian language indicators, including the consistent use of Russian language in malware code over the course of six years.
I want you to see certain comments or coding styles that are the same or similar to someone else’s (because I reuse other people’s code.)
Fidelis Security, another well-known cyber security company, was provided samples of the Cozy Bear and Fancy Bear malware for “independent analysis.” According to Fidelis, these samples matched the description provided by CrowdStrike and “contained complex coding structures and utilized obfuscation techniques that we have seen advanced adversaries utilize in other investigations we have conducted,” Michael Buratowski, the senior vice president of security consulting services at Fidelis, noted. The malware was “at times identical to” malware that other cyber security vendors, such as Palo Alto Networks, have attributed to Fancy Bear. Many of these similarities have been previously identified by other cyber security vendors and made public as far back as 2013.
I want you to see data about compilation date/time, PDB file path, etc., which could lead you to draw erroneous conclusions have no bearing on malware behavior or capability.
FireEye, in its report on APT-28 (i.e., Fancy Bear), also notes that the compile times associated with the malware align with the work hours and holiday schedules of someone residing in the same time zone as Moscow and St. Petersburg.
The fascinating thing about Michael Tanji’s observations was that they were made in 2012, largely in response to the spate of China attributions headed up by Dmitri Alperovitch’s highly publicized 2011 Shady Rat report. Four years later, the fixation on pattern-derived attribution remained a problem within the cyber security collective, this time with Russia as the target de jour. In 2011, the Chinese caseload was spread across a broad field of separate cyber attacks. In 2016, the Russian data set was limited to a single event — the DNC cyber attack.
Moreover, the data set in 2016 was under the exclusive control of a single entity — CrowdStrike. While select malware samples were farmed out to like-minded vendors, for the most part outside analysis of the DNC cyber penetration was limited to the information provided by CrowdStrike in its initial report. Even the FBI found itself in the awkward position of being denied direct access to the DNC servers, having instead to make use of “forensic images” of the server provided by CrowdStrike, along with its investigative report and findings.
There is much unknown about these scans — were they taken from May 6, when CrowdStrike first detected what it assessed to be a Russian presence inside the DNC server? Or are they from June 10, the last day the server was in operation? The difference could be significant, keeping in mind the fact that there were more than 30 days between the two events.
In this intervening time, CrowdStrike watched Guccifer 2.0 exfiltrate documents. It also possibly engaged in offensive measures, such as the dangling of so-called “attractive data” (the Russian-language tainted opposition research documents come to mind.) The possibility of additional manipulation of data cannot be discounted. However, even though members of Congress are starting to call for the FBI to take physical possession of the server and conduct its own independent forensic investigation, the server remains in the possession of the DNC.
Through the release of its “Bears in the Midst” report, CrowdStrike anticipated that the US government and, by extension, the American people, would place their trust in CrowdStrike’s integrity regarding Russian attribution. The media has, for the most part, accepted at face value CrowdStrike’s Russian attribution regarding the DNC cyber attack.
The US government, while slower to come onboard, eventually published a Joint Statement by the Office of Director of National Intelligence and the Department of Homeland Security in October 2016 that declared, “The recent disclosures of alleged hacked e-mails…by the Guccifer 2.0 online persona are consistent with the methods and motivations of Russian-directed efforts.”
On December 29, 2016, the FBI and DHS released a Joint Analysis Report (JAR) that directly attributed the presence of both the Cozy Bear and Fancy Bear actors on the DNC server to “spearfishing” attacks, thereby eliminating from consideration any possibility that Guccifer 2.0 penetrated the DNC server through a “zero day” exploit. This was a curious assessment, given that the only data in existence regarding what had transpired inside the DNC server was the data collected by CrowdStrike — data CrowdStrike maintains did not provide evidence pertaining to how the DNC server was initially breached by either Cozy Bear or Fancy Bear.
The Director of National Intelligence followed up with a National Intelligence Assessment, released on January 6, 2017, that similarly endorsed the findings of CrowdStrike when it came to Russian attribution for the Cozy Bear and Fancy Bear penetration of the DNC, as well as linking Guccifer 2.0 to the GRU, or Russian military intelligence. It was the strength of this national assessment that closed the book on debate on the matter of Russian attribution. Senators and Congressmen, intelligence officials and media pundits — all seem to be in agreement that Russia was singularly responsible for the cyber attack against the DNC, and the subsequent release of documents acquired from that breach. “Without a doubt,” “undeniable,” “incontrovertible” — this was the verbiage that accompanied any discussion of the case against Russia.
The genesis moment for this collective clarity, however, remains the carefully choreographed release of the CrowdStrike report, “Bears in the Midst,” and the accompanying Washington Post exclusive laying the blame for the DNC cyber attack squarely at the feet of Russia. From this act all else followed, leading to the certainty that accompanied this attribution was enough to overcome the challenge posed by the sudden appearance of Guccifer 2.0, enabling the same sort of shoehorned analysis to occur that turned Guccifer 2.0 into a Russian agent as well.
Much of this discussion turns on the level of credibility given to the analysis used by CrowdStrike to underpin its conclusions. Alperovitch, the author of the “Bears in the Midst” report, does not have a good record in this regard; one need only look at the controversy surrounding the report he wrote on Shady Rat while working for McAfee. A new report released by Alperovitch and CrowdStrike casts further aspersions on Alperovitch’s prowess as a cyber analyst, and CrowdStrike’s overall methodology used to make its Russian attribution.
On December 22, 2016, CrowdStrike published a new report purporting to detail a new cyber intrusion by the Fancy Bear actor, titled “Danger Close: Fancy Bear Tracking of Ukrainian Field Artillery Units.” This analysis, prepared by Adam Meyers, CrowdStrike’s vice president for intelligence, was claimed to further support “CrowdStrike’s previous assessments that Fancy Bear is likely affiliated with the Russian military intelligence (GRU). This report was used to promote a Jan. 4 live discussion event with Meyers and Alperovitch, titled “Bear Hunting: History and Attribution of Russian Intelligence Operations,” which was intended to educate the audience on the links between Fancy Bear and the GRU.
The “Danger Close” report was presented as further validation of CrowdStrike’s Falcon Program, which CrowdStrike claims helps organizations stop cyber penetrations through proactive measures developed through a deep understanding of the adversary and the measures needed to stop them. It was Falcon that “lit up” ten seconds after being installed on the DNC server back on May 6, 2016, fingering Cozy Bear and Fancy Bear as the culprits in the DNC attack. Falcon was now being linked to this newest effort at Russian attribution.
The only problem for Meyers, Alperovitch and CrowdStrike was that “Danger Close” was wrong — dead wrong — in every aspect of its analysis. The report was dissected by none other than Jeffrey Carr — the same individual who criticized Alperovitch over his Shady Rat claims. One of Carr’s most important findings deals directly with the credibility methodology used by CrowdStrike to attribute Fancy Bear to the GRU. “Part of the evidence supporting Russian government involvement in the DNC and related hacks (including the German Bundestag and France’s TV5 Monde),” Carr writes, “stemmed from the assumption that X-Agent malware was exclusively developed and used by Fancy Bear. We now know that’s false, and that the source code has been obtained by others outside of Russia.” Carr cites at least two examples, one a security company, the other a hacker collective, of the X-Agent malware existing “in the wild.” If these two entities have the X-Agent malware, Carr notes, “then so do others, and attribution to APT28/Fancy Bear/GRU based solely upon the presumption of ‘exclusive use’ must be thrown out.”
In one fell swoop, Carr destroyed the very premise upon which CrowdStrike not only attributed the DNC cyber attack to Russia, but the heart and soul of CrowdStrike’s business platform — the Falcon Platform used by CrowdStrike to provide “end point” protection to its clients. Far from representing an intelligent platform capable of discerning threats through advanced algorithms and proprietary techniques, the Falcon Platform seems to be little more than a database pre-programmed to deliver a preordained finding — X-Agent equals Fancy Bear, and Fancy Bear equals Russia.
Also, metadata analysis by an independent researcher which contradicts the 'Russia Hack' narrative:
https://theforensicator.wordpress.com
Forensicator maintains his position that the most probable and plausible interpretation of the observations derived from the NGP VAN 7zip metadata is:
There is evidence that suggests the files in the NGP VAN archive were copied (twice) locally, on the East Coast, US. Further, there are indications that a USB-2 capable media may have been used for the first copy operation on July 5, 2016 and that a FAT-formatted media was used in the second copy operation on Sept. 1, 2016. (A USB flash drive is one of the most popular FAT-formatted media, but there are others including SD cards and removable hard drives.)
Essentially: files eventually published by the Guccifer 2.0 persona were likely initially downloaded by a person with physical access to a computer possibly connected to the internal DNC network. The individual most likely used a USB drive to copy the information.
Heaven Swan wrote:I’m still baffled as to why so many Americans and RI posters have such a hard time believing that Russia could be actively cyber attacking the US and that the Skripal poisoning and anything and everything Russia is accused of doing is baseless propaganda against “the bear.”
alloneword wrote:[...]
I painstakingly went through much of the material offered up by 'crowdstrike' et al as evidence of 'Russian Hacking" and found them to be utterly unconvincing. I sought more learned opinions from within the infosec community and heard nothing to make me alter that view, and quite a lot to confirm it. I find the idea that the DNC leak was not perpetrated by an individual (most likely Seth Rich), but rather "Russian Hackers", to be unsupported by the facts
alloneword wrote:scene 1 act 1... The first thought to occur to me on hearing the finger-pointing at Russia was "Why would the Russians exhibit such poor tradecraft?".
Let's put it another way... If you're asking me to believe that this was the work of the Russian State, you're asking me to believe that they stockpiled and hid such 'nerve-agents' from OPCW inspections, only to reveal their deceit on the world stage in order to bump off a burned nobody that they'd pardoned and 'swapped' eight years previously. It makes no sense whatsoever. You'd have to believe the Russians to be pretty stupid. I don't.
So then we have all the scare-stories about members of the public being treated for 'nerve-agent poisoning' etc, only to hear word from a well respected medical professional (who happened to be to person actually there, doing the treating) 'that no patients have experienced symptoms of nerve-agent poisoning in Salisbury and there have only ever been three patients with significant poisoning'.
And now we have the spectacle of Porton Down telling us:
British scientists at the Porton Down defence research laboratory have not established that the nerve agent used to poison Sergei and Yulia Skripal was made in Russia, it has emerged.
While our own Foreign Secretary, Boris Johnson told us only last week:
You argue that the source of this nerve agent, Novichok, is Russia. How did you manage to find it out so quickly? Does Britain possess samples of it?
Let me be clear with you … When I look at the evidence, I mean the people from Porton Down, the laboratory …
So they have the samples …
They do. And they were absolutely categorical and I asked the guy myself, I said, "Are you sure?" And he said there's no doubt.
So who to believe? The Consultant who actually treated these people, or the Foreign Secretary who is clearly lying to exaggerate 'baseless propaganda'?
JackRiddler wrote:We are where we are because of the breaking of the promise not to expand NATO, the plunder of Russia by Western-guided shock therapy and mafia-run privatization under the heavily CIA-backed Yeltsin, the Bushist withdrawal from the ABM treaty and the war of aggression on Iraq, joint exercises targeting Russia as the future adversary, the paranoia (historically determined but still unhinged) in "New Europe" Poland and Co., the U.S. machinations to flip Ukraine by coup rather than election (which would have happened), and the heavy U.S.-Gulf States intervention to turn anything that might have been a Syrian revolution (which would have lost, but with a lot fewer casualties) into an opening for the worst international jihadi death-festival in history (partly as an escalation in response to the Iranian intervention on Assad's behalf, but nothing makes it right!).
The Russian state and even Putin himself were goaded into increased "Putinism," and now the goading and the Putinist ideology are symbiotic. Putinism (by which I mean this show of political authoritarianism and scapegoating) lives off "the West's" constant theater (and reality) of physical threat. Things could have totally gone in another direction, back when the ball was in the U.S. court to choose.
viewtopic.php?f=8&t=38295&p=654042&hilit=Russia#p654042
We can go further back to WWII, and consider the incredible suffering, destruction and loss of life endured by Russians and others in the USSR, all of which I think help inform Russian foreign policy attitudes. That is to say, I don't think many of them are itching to get into another world war.
UK government deletes tweet about Russian spy's poisoning
By James Masters, Sheena McKenzie, Gianluca Mezzofiore and Katie Polglase, CNN
Updated 1348 GMT (2148 HKT) April 4, 2018
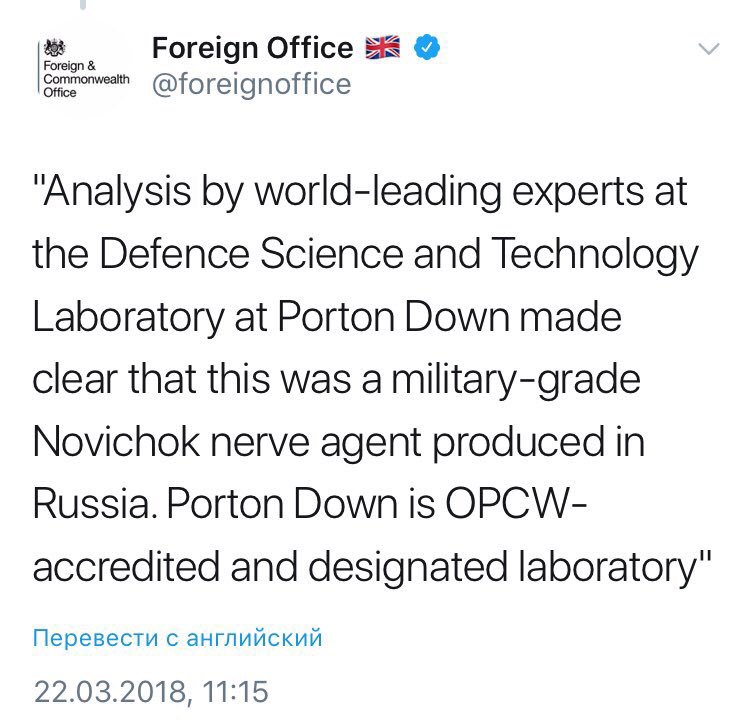
London (CNN)Britain's claim that Moscow was behind the poisoning of a former Russian spy faced fresh scrutiny Wednesday when it emerged the UK government had deleted a tweet blaming Russia for producing the nerve agent used in the attack.
The UK Foreign Office acknowledged it had removed the social media post, which stated that British chemical weapons experts believed Russia made the nerve agent, Novichok, used to poison Sergei Skripal and his daughter Yulia in the English city of Salisbury on March 4.
A Foreign Office spokesperson told CNN that the tweet was removed because it was "truncated and did not accurately report" a briefing by the British ambassador to Moscow last month.
The revelation came as the UK government was already on the defensive on the issue. On Tuesday, the chief executive of the Porton Down defense laboratory in the UK said scientists could not confirm where the nerve agent was made. The British government insisted that additional material from intelligence sources led it to the conclusion that Russia was behind the attack.
Russia, which has repeatedly denied involvement in the attack and has sought to blame Britain instead, seized on the developments. The Russian embassy in London tweeted: "Why would @foreignoffice delete this tweet from 22 March?"
The controversy centered on a briefing on the Salisbury poisoning given by the British ambassador to Moscow, Laurie Bristow, on March 22. In it, he said "the analysts at Porton Down, the Defense Science and Technology Laboratory in the UK, established and made clear that this was a military-grade chemical weapon. One of the Novichok series; a nerve agent as I said produced in Russia."
A tweet, which the Foreign Office said was published in "real time", paraphrased the comments, saying: "Analysis by world-leading experts at the Defence Science and Technology Laboratory at Porton Down made clear that this was a military-grade Novichok nerve agent produced in Russia."
The tweet was deleted sometime before March 27. An identical tweet by the UK embassy in Russia, was also deleted.
https://edition.cnn.com/2018/04/04/europe/salisbury-uk-government-deleted-tweet-intl/index.html
BenDhyan » Wed Apr 04, 2018 8:43 pm wrote:UK government deletes tweet about Russian spy's poisoning
A Foreign Office spokesperson told CNN that the tweet was removed because it was "truncated and did not accurately report" a briefing by the British ambassador to Moscow last month.
...
(my emph.)Laurie Bristow said, not wrote:...the analysts at Porton Down, the Defence Science and Technology Laboratory in the UK, established and made clear that this was a military-grade chemical weapon. One of the Novichok series; a nerve agent as I said produced in Russia...
There is also no doubt that Novichok was produced in Russia by the Russian state. It is not a weapon that can be manufactured by non-state actors. It is so dangerous it requires the highest grade state laboratories and expertise to produce it...
So the fact that the Novichok was produced in Russia, the fact that Russia has a history of state-sponsored assassinations, and the fact that Russia has responded with the usual playbook of disinformation and denial left us with no choice but to conclude that this amounts to an unlawful use of force by the Russian state against the United Kingdom.
Users browsing this forum: No registered users and 8 guests